
The latest information technology news from around the world. Covers computers, tips and tricks, operating systems, company announcements, product reviews, and much more.
- Krebs On Security
- Computer World
- BBC News
- Windows Central
- Windows Report




Asana has launched AI Studio, a no-code tool for building generative AI agents that can automate work planning tasks.
The company first unveiled its “AI teammate” plans in June, promising to enable customers to build autonomous agents that can perform tasks independently within the work management app.
On Tuesday, Asana said that the AI agent builder — renamed Asana AI Studio — is now out of beta and available to customers on its Enterprise and Enterprise+ plans in “early access.” There are two options for accessing AI Studio at this stage: a free plan with daily limits on usage, and a paid add-on. (Asana declined to provide specifics on pricing.)
Customers trialing AI Studio during the beta noted several advantages when deploying AI agents, said Paige Costello, head of AI at Asana. “The key benefits we’re seeing are the speed of decision-making and the overall acceleration of work and reduction in administrative and busy work,” she said.
“There is tremendous potential in AI-based agents to expedite workflow,” said Wayne Kurtzman, research vice president covering social, communities and collaboration at IDC. “The ability to deploy agents in the stream of work, where teams work, and without code becomes a powerful proposition.”
With the launch, Asana also announced additional features for AI Studio. These include a wider variety of potential AI agent actions, more control over smart workflow capabilities such as data access and costs, and an increase in the amount of context the AI agent can reference in its decision-making.
Users can also view a record of an AI agent’s actions and decisions. “You can actually dig into work that has happened and understand why the custom agent that you’ve built made a specific choice and undo the selection that it’s done,” said Costello.
Users can choose from four language models to power AI agents: Anthropic’s Claude 3.5 Sonnet and Claude 3 Haiku, and OpenAI’s GPT-4o and GPT-4o mini.
With AI agents able to complete tasks autonomously, the propensity for language models to “hallucinate” and provide inaccurate outputs could be a concern for businesses. Costello said there are safeguards in place to help reduce the likelihood of AI agents generating and acting on incorrect information, and argued those designing the AI- workflows are “in the driver’s seat.”
For example, a user can require an AI agent to seek human approval before carrying out actions deemed higher risk, such as sending an external email to a customer. “People are the decision makers –– they’re the ones ultimately accountable for work,” said Costello.
Adoption of AI agents is at an early stage for most organizations, but it’s accelerating, said Margo Visitacion, vice president and principal analyst at Forrester, covering application development and delivery. Successful deployments will require “experimentation, failing fast, and learning from those experiments,” she said.
“It takes the right level of oversight, focus on the problems you’re solving, and gathering feedback to ensure you’re using the right model that suits your needs,” said Visitacion.

Artificial Intelligence continues to dominate this week’s Gartner IT Symposium/Xpo, as well as the research firm’s annual predictions list.
“It is clear that no matter where we go, we cannot avoid the impact of AI,” Daryl Plummer, distinguished vice president analyst, chief of research and Gartner Fellow told attendees. “AI is evolving as human use of AI evolves. Before we reach the point where humans can no longer keep up, we must embrace how much better AI can make us.”
Continue reading on Network World for Gartner’s top predictions for 2025.

We waited three years for Apple to update the iPad mini, and what we got is more of the same — boosted with a much better processor. Apple’s iPad mini has consistently been positioned as either the most versatile, or the most underpowered tablet in the company’s lineup. That’s changed with the latest iteration, which remains small enough to take anywhere, but also becomes much more powerful than ever, thanks to a new A17 Pro chip.
Whole lotta processorIf you’ve used an iPad mini before, you know what you’re getting: a reliable, powerful, and eminently mobile device with a large display you can slip inside an inner coat pocket and use just about anywhere, except in the rain.
Available in two new colors (four in all, including space gray, starlight, purple, and blue), the chip is the real substance here. Apple promises a 30% faster CPU, a 25% increase in GPU performance, and double the machine learning performance of the last-generation iPad mini. Even in comparison to the last model, that processor means you really will feel the difference in terms of performance — and the internal memory has been beefed up to 8GB, which also makes a big difference.
Geekbench 6 tests on the review device generated single-core results of 2,520 and 6,440 on multi-core performance. In comparison, the iPad mini 6 with an A15 Bionic chip achieved 2,121 single-core, and 5,367 multi-core scores. While aggregate test results will be more accurate, my own testing confirms substantial improvement in the processor. What you are getting is an iPad that will (a) run Apple Intelligence, and (b) deliver the performance you require to run apps for the next few years.
That’s great for consumer users, but also important to education and enterprise deployments. This is, after all, an iPad that seems a good fit for real-world business applications such as retail, hospitality, warehousing, or distribution. You’ve probably already seen it used in one of those fields, so the processor upgrade will be a significant benefit for firms seeking to deploy AI solutions within their digital transformation efforts.
I recently learned that pilots sometimes fly with an iPad mini so they can use it to check flight maps and flight support apps while they are in the air. They (and their passengers) should be happy with the lack of lag and hardware-accelerated ray tracing they get while using those apps in flight.
 Apple
The song remains the same
Apple
The song remains the same
The display remains the same — in this case, the well-received Liquid Retina system we saw last time around. You can expect a wide range of supported colors at 2255×1488-pixel resolution (at 326ppi) and a nice and bright 500 nits. What changes is you now also gain Wide Color P3 support and support for True Tone. (The latter uses advanced sensors to adjust the color and intensity of your display to match the ambient light, so images appear more natural.)
I’ve been testing the iPad mini for a few days and have not experienced any cases of so-called “jelly-scrolling,” when one side of the screen refreshes at a different rate than the other when scrolling up and down.
When it comes to most of the hardware, the music hasn’t changed. You’ll still find it an easy-to-hold device because it is light, thin, and small. Dimensions remain 7.7 x 5.3 x 0.25 inches. The weight is 0.65 pounds, same as the last generation. You get USB-C (though this supports data transfers at 10Gbs, twice as fast as before), Touch ID, and no headphone port.
Under-the-hood changes are all about networking — Wi-Fi 6E, 5G support, and Bluetooth 5.3. The cameras remain more or less the same, though images captured on the device use machine intelligence to optimize the results. One older image Apple Intelligence selected as my Home screen picture really pops thanks to the AI tweaks.
Good times, AI timesNow, for most mortals, Apple Intelligence remains something that’s nice to have, rather than something essential. That’s how it will remain until the first services under that moniker appear next week. On this device, one thing Apple Intelligence is already good at is summarizing emails and helping write better ones, while the Siri improvements in iOS 18.1 bode well for additional contextual intelligence expected to appear next year.
Given that Apple Intelligence isn’t available yet and won’t be available for some time in China or Europe, it’s too early to surmise the extent to which that will change the user experience. But even while that jury remains out, iPad Air continues to keep its promise to provide a good balance of mobility and usable display space. Its processor also gives third-party AI developers a platform on which to build other non-Apple AI-augmented experiences. That could be useful to some businesses. (And business and education users might appreciate that the camera takes excellent document scans.)
 Apple
Bad times
Apple
Bad times
One complaint concerns the screen refresh rate. While other tablets have already jumped to 120Hz, the iPad mini remains confined to 60Hz. I don’t know if that decision is based on costs, heat dissipation, energy management, or parsimony, but I have seen enough people commenting on this to know that it’s something Apple will need to deal with in the future.
If you are using an Apple Pencil with your current iPad mini, I have bad news: the new model will not support any Apple Pencil other than the newish Apple Pencil Pro and the USB-C Apple Pencil. If you’ve been using a second-generation Apple Pencil, you’re out of luck. (First-generation pencil support in iPad mini disappeared with iPad mini 6.)
It is also interesting that Apple continues to avoid kitting out its iPad mini or standard iPad with the M-series chips found inside the iPad Air and iPad Pro. The decision makes it clear that Apple is ultimately using the built-in processor as its way to compete with itself, as no one else in the tablet market is really in its league. Want a more performant tablet? Apple has them, but not in the mini range.
Finally, when it comes to the built-in camera, you probably have a better camera in your smartphone than what’s here. It’s good enough, has been updated to deliver better, and Apple’s image intelligence software means it takes good pictures, if you want to do so with a tablet. It is more than suitable for video conferencing, of course.
What else to knowThere is one more thing, the price. Just as in 2021, the entry-level model still costs $499 (Wi-Fi only, add $150 for the cellular model), but it now ships with 128GB of storage rather than 64GB; 256GB and 512GB models are also available. More storage is always a win, but don’t ignore that Apple Intelligence requires at least 4GB of that space for its own use.
Should you buy it?I’ve used iPads since the beginning. Over that time, my preferences have kind of coalesced around the iPad Air, which I think provides a brilliant balance between power and affordability, and the iPad mini, which I rate highly for its inherent portability, but always deserved a little more power.
The move toboost internal storage and memory while pepping things up with an A17 Pro chip means the small device can handle most tasks; you probably won’t be using it extensively for video processing in the field or advanced image editing, but could use it for some of both of those tasks. You’ll also enjoy reading books, gaming, watching videos, or listening to music. (Apple’s audio teams really know how to create great soundscapes in these devices.)
The processor upgrade means that if you are using an iPad mini 6 or earlier, a move to this model makes sense — particularly if you want to explore what Apple Intelligence is all about. While it’s mostly the same, it is overall better, and if you’ve convinced yourself you have a solid reason to invest in a smaller tablet, the iPad mini 7 remains the best small tablet around.
Please follow me on LinkedIn, Mastodon, or join me in the AppleHolic’s bar & grill group on MeWe.

Generative AI is on track to transform entry-level roles across industries, with 64% of leaders expecting these positions to evolve from creation to review and refinement of outputs within the next three years. The percentage of managers holding a similar view stood at 71%, according to new research from the Capgemini Research Institute.
The findings suggest the traditional model of junior employees manually creating content, data, or code is rapidly being replaced by generative AI, which can generate these outputs in a fraction of the time. As a result, employees in these positions will focus more on quality control, critical analysis, and ensuring AI outputs meet business standards, the report added.
The findings are based on Capgemini Research Institute’s May 2024 survey that involved 1,500 executives and 1,000 entry-level employees from 500 organizations with over $1 billion in revenue, to explore generative AI adoption.
The report revealed that employees expect genAI will manage an average of a third of their tasks (32%) within the next 12 months, indicating a potential productivity boost. This shift is expected to be felt most acutely in roles that traditionally involve manual content creation, data entry, or routine customer service tasks.
“Generative AI tools are becoming more adept at assisting with complex managerial tasks, which could challenge the status quo of organizational structure and ways of working,” Roshan Gya, CEO of Capgemini Invent and a member of the Group Executive Committee said in a press note. “This shift allows employees to focus on higher-value activities, unlocking new perspectives and challenging assumptions.”
Increased autonomy for junior employeesThe widespread integration of AI into the workplace will not only change the nature of entry-level work but also grant more autonomy to junior employees.
According to the data, 52% of leaders and managers expect entry-level positions to gain greater independence as AI becomes more embedded in daily workflows. For example, in industries such as supply chain and logistics, AI will take on tasks like inventory management and order processing, allowing junior analysts to focus on strategic tasks and project management.
As AI continues to manage mundane tasks, junior employees will have more opportunities to make decisions that were previously the domain of higher-level staff. This will enable them to fast-track their careers and assume greater responsibilities early on, the report stated.
The report reveals that 51% of leaders believe AI will accelerate the career progression of entry-level employees. With AI automating routine functions, junior employees will gain exposure to more strategic elements of their roles, moving into management positions much faster than traditional career paths have allowed. AI will facilitate this shift by providing employees with the tools and data necessary to make informed decisions and take on supervisory roles.
“It should be noted that this shift depends on several factors: clarity on skills requirements at higher levels; the ability of junior employees to develop these skills (often tied to experience, which cannot be fast-tracked); and the availability of opportunities available for the shift,” the report pointed out.
It further added, “Organizations must prioritize building the skills and readiness of junior employees as part of a clear roadmap for employees’ journeys to people leadership or functional/technical leadership. This requires proactive steps around talent acquisition, development, skilling, and review and reward mechanisms.”
This transformation is already visible in fields such as marketing, customer service, and even technical domains like software development.
“We’re seeing AI take over foundational tasks in these sectors, and junior employees are becoming curators of AI work, rather than creators,” the report said.
With AI’s involvement, the proportion of managers within teams could expand from 44% to 53%, reflecting a broader move toward specialized roles that focus on managing AI-human collaborations.
Productivity gains, but upskilling gaps remainThe findings from the report suggest that while AI adoption promises significant productivity gains — potentially saving 18% of time for entry-level workers — there are concerns about the readiness of employees to leverage these tools.
Despite the optimism about AI’s role in career acceleration, the report highlights a significant gap: only 16% of employees feel they are receiving adequate training in AI-related skills from their organizations. This gap poses a major challenge for companies that want to fully harness the benefits of AI, especially at the entry level.
“Without the proper training and resources, employees won’t be able to maximize the potential of AI,” the report cautioned, urging organizations to prioritize formal training programs to ensure their teams are ready for the AI-driven future.
The path aheadDespite the promise of genAI, adoption remains nascent. While 64% of workers already use genAI tools, only 20% use them daily, the report stated.
This gap between AI’s potential and actual usage underscores the need for clearer guidelines, comprehensive training, and better integration of AI tools into existing workflows. As organizations continue to explore AI’s capabilities, defining roles and responsibilities for human-AI collaboration will be key to ensuring accountability and cohesion across teams.
With 81% of leaders expecting new roles like AI ethics specialists and data curators to emerge, the landscape of entry-level work is on the verge of a significant transformation. The future of work, it seems, will be less about replacing human effort and more about enhancing it through strategic collaboration with AI.

Saying the legal profession is document-intensive is like claiming that a library is filled with books. Unlike researchers using the Dewey Decimal System, though, lawyers face an ocean of big data from which they must fish out case evidence.
For more than a decade, law firms have been using machine learning and artificial intelligence tools to aid the discovery process, helping them hunt down paper trails and digital content alike. But it wasn’t until the arrival two years ago of OpenAI’s generative AI (genAI) conversational chatbot, ChatGPT, that the technology became common and easy enough to use that even first-year associates straight out of law school could rely on it for electronic discovery (eDiscovery).
The interest in genAI for legal discovery and automating other tasks is unprecedented, according to Ron Friedmann, a Gartner senior director analyst.
“There’s way more piloting that I’ve seen, especially in large law firms. So, there’s been a lot of expense, especially the allocating of staff and paying out of pocket for licensing fees,” Friedmann said.
“Part is keeping up with the Joneses, part of it is marketing, and part of it is just getting over the adoption challenges,” he continued. “In eDiscovery, before the advent of genAI, you needed some training to know how to interact with discovery database. There were a lot of tools, but they all had the same issue: You had to be pretty technically adept to tackle the database yourself.”
Law firms and corporate legal departments are adopting genAI for a myriad of purposes, ranging from document discovery and analysis to contract lifecycle management. GenAI can be used to categorize and summarize documents, draft new ones, and generate client communications.
A 2023 American Bar Association survey found that over 20% of large law firms (500+ attorneys) are using AI tools, with nearly 15% considering purchasing them. And over the past year, AI adoption in the legal sector has jumped from 19% to 79%, according to legal tech firm Clio.
All areas of law will use genAI, according to Joshua Lenon, Clio’s Lawyer in Residence. That’s because AI content generation and task automation tools can help the business side and practice efforts of law firms. However, areas that have repetitive workflows and large document volumes – like civil litigation – will adopt genAI e-discovery tools more quickly. Practice areas that charge exclusively flat fees – like traffic offenses and immigration – are already the largest adopters of genAi.
Lenon said AI is expected to have the most immediate impact in areas like civil litigation, where repetitive workflows and large volumes of documents make it ideal for tasks such as eDiscovery.
“Additionally, practice areas that commonly rely on flat-fee billing, such as traffic offenses and immigration, are already leading in the adoption of genAI tools. The efficiency gains in these sectors are driving their early and widespread use of AI,” Lenon said.
In legal departments, for example, genAI has allowed workers to query digital contracts and get accurate answers to questions about things like existing clauses.
“There are all sorts of things buried inside contracts that once people can easily get access to will have a big impact on how companies operate, the risk they have, and how to mitigate those risks,” said David Wilkins, director of the Center on the Legal Profession at Harvard Law School.
Wilkins and other experts say that because law is document intensive, people have long sought ways to use technology to streamline, make more efficient, and cut down on work related to the discovery, creation, and analysis of documents.
“What we’re seeing now is lots of use of technologies of various kinds in contract formation and end-to-end contract lifecycle management. That is a huge area,” Wilkins said.
Corporate legal departments are not as far down the genAI adoption path as law firms, because companies primarily see those business units as cost centers — so the purse strings are cinched tighter. Nonetheless, legal departments are kicking the tires on genAI.
A clear win for pre-trial discoveryMultinational law firm Cleary Gottlieb said it has been able to dramatically cull the number of attorneys used for pre-trial discovery and has even launched a technology unit and genAI legal service: ClearyX.
In the past, it wasn’t uncommon for 150 or more attorneys to be assigned to a case to discover all the documents and other content, and it could take them months to complete the task.
While Cleary readily admits that genAI isn’t perfect in retrieving 100% of the documents related to a case or always creating an accurate synopsis of them, neither are humans. At this point in the technology’s development, it’s good enough most of the time to reduce workloads and costs.
Christian “CJ” Mahoney, global head of Cleary’s e-Discovery and Litigation Technology group, said he was just part of a lawsuit that involved analyzing 50 million documents (15 terabytes of data). “And we had to do it in matter of weeks to find out what we had to provide to the opposing party.
“We’re using more complex workflows using AI. I saw a 60-person to 45-person reduction. But on this kind of case, I would have had probably 150 attorneys doing this 15 years ago. Back then, it would just be like ‘OK, guys, here’s a mountain of evidence — go through it,’” Mahoney said.
Traditional ways to look through case documents simply aren’t feasible anymore. “You need to incorporate AI into the process for analysis now,” Mahoney said.
While his firm has been using machine learning and AI for about a decade, with the introduction of genAI, there’s ubiquity and ease of use, Mahoney said. That has allowed even junior associates to be able to use the tech for eDiscovery and other tasks.
“There’s a bit of an expectation that with the advent of genAI, things should be quicker and cheaper,” he said.
Carla Swansburg, CEO of ClearyX, the firm’s AI tech subsidiary, said that as recently as a year and a half ago, clients were telling her AI is too risky, but those same clients are now asking how Cleary is using AI to benefit them and make their services more efficient.
“Nobody went to law school to do this. I used to go through banker’s boxes with sticky notes as a litigator. Nobody wants to do that. Nobody wants to read 100 leases to highlight an assignment clause for you,” Swansburg said. “The good thing is [genAI is] moving up the value chain, but it’s starting with things that people really don’t want to be doing anyways.”
The interest in genAI hasn’t been lost on those selling traditional legal services and software. For example, legal research tools such as LexisNexis, Westlaw, and vLex and legal document automation software from Harvey.ai and Clio have built genAI into their products. Contract lifecycle management and analytics vendors such as Icertis, Sirion, LinkSquares, and Ironclad have also added AI to their lines.
The number of proven and routine use cases for genAI in legal fields is limited, however, because of ongoing accuracy and hallucination problems, according to Friedmann. And genAI isn’t always less expensive than using people.
“We are still trying to collectively figure out what the economics of it is. I’ve spoken to friends who say in the end genAI took more time and cost than doing it the old-fashioned method,” Friedmann said. “But people are remaining open to it and continuing to experiment.”
The death of the billable hour?Over the past two decades, the vast volumes of structured and unstructured data generated through traditional means, such as contracts, records, corporate policies, and so on has been joined by electronic communications — adding new challenges in eDiscovery.
Once only a paper chase, legal discovery now involves scouring emails, messaging, social media records — even video and photos — in the lead-up to a trial.
Nearly three-quarters of a law firm’s hourly billable tasks are exposed to AI automation, with 81% of legal secretaries’ and administrative assistants’ tasks being automatable, compared to 57% of lawyers’ tasks, according a survey of both legal professionals (1,028) and another adults (1,003) in the U.S. general population, by Clio.
Hourly billing has long been the preference of many professionals, from lawyers to consultants, but AI adoption is upending this model where clients are charged for the time spent on services.
In 2023, 19% of law firms reported using AI. Now, 79% of legal professionals are using AI in their practice, according to legal tech company Clio.
As AI adoption continues to accelerate in the legal industry, executives may need to rethink key elements of their business, including their billing models. Billable work could be automated by AI, according to experts.
This month, Clio released the results of a survey showing that law firms are charging 34% more of their cases on a flat-fee basis compared to 2016.
The billable hour will continue, but the frequency of use and types of activities that will be billed hourly will diminish. Automatable tasks will switch to flat fees, with the AI output being reviewed at hourly rates,” said Clio’s Lenon. “The billable hour is unlikely to be fully eliminated, but its dominance in the legal industry is expected to decrease. AI-generated outputs, particularly those requiring human review, may still be billed on an hourly basis.
“Ultimately, the billable hour will remain, but in a more selective capacity,” Lenon continued.
Clio’s research over 7,000,000 time entries found that 74% of billable legal work activities will be impacted by AI automation.
While hourly billing remains predominant in law firms, their clients are driving the shift towards flat fees, with 71% now preferring to pay a flat fee for their entire case, and 51% favoring flat fees for individual activities, according to Clio’s report.
In addition, law firms using flat fees benefit from quicker billing cycles and faster payment collection, as they are five times more likely to send bills — and nearly twice as likely to receive payments — as soon as they complete their work for clients.
Last year, firms were testing on average as many as three to five genAI models in the hope of reducing workloads, and that also meant employing supportive resources such as innovation teams and knowledge management professionals, Gartner’s Friedmann said.
People have been talking about the demise of the billable hour for about 30 years “and nothing’s killed it yet,” said Ryan O’Leary, research director for privacy and legal technology at IDC. “But if anything will, it’ll be this.”
However, there are still a lot of issues with genAI that need to be settled before it could automate legal services, O’Leary cautioned — not least of which is how much genAI may cost to use and how accurate and secure it can be.
“The cost of using AI may be as much as using an associate,” O’Leary said.
Is genAI cheaper and more accurate than an attorney?Along with AI’s ability to perform tasks previously accomplished by attorneys and other legal workers, there remains a big concern over accuracy, security, and hallucinations. As in the healthcare industry, the stakes are high when it comes to client confidential information.
“There are big issues around copyright protection and whether these large language models are being trained on copyrighted materials,” Harvard’s Wilkins said. “So, what you’re seeing is a lot of experimentation with trying to build customized AI models and large language models. AI providers claim their models are trained exclusively on legal materials, cutting down on hallucinations.”
While law firms are aware of AI’s pitfalls, attorneys are still going to use the technology, Wilkins said, whether or not that’s in line with a corporate policy. GenAI is simply too “transformative” a technology to not use simply because there are risks, he said.
One problem in comparing human workers to the technology is that the bar is often set too high for AI, Wilkins said.
“I’ve heard people say, ‘We could never use this unless it’s 98% effective and reliable.’ I said, ‘Well, does it have the reliability of sending an associate to a windowless warehouse in Phoenix, Arizona to find documents related to a case? Is that 99% accurate?’” Wilkins said.
In the end, whether genAI assists in a task or not, ultimately the attorneys involved will be held responsible for the outcome — good or bad. Whether the technology will replace attorneys and legal aides remains to be seen.
“Our experience has been — and we’ve kicked tires on a lot of language models and purpose-designed tools — [genAI tools] are not good enough to replace people for a lot of the work we do,” ClearyX’s Swansburg said. “For something like due diligence…, you often must be [100%] right. You need to know whether you can get consent to transfer something. In other use cases, such as summarization and initial drafting, that sort of thing is a little more accessible.
“In my world, it’s not really replacing jobs yet, but it’s changing how you do jobs,” she continued. “So, it’s allowing people to move up the value chain a little bit. It’s taking away rote and repetitive work.”
Harvard’s Wilkins placed the adoption of AI by law firms and other legal entities as still being “in the Stone Age” but with massive potential.
“The potential efficiencies are great,” he said. “We’re just working out what are the real advantages.”

Gartner is sharing its annual look at the hot technologies enterprise customers should be watching out for in the coming years. AI, security, energy-efficient computing, robotics, and virtual computing interactions are among the research firm’s top 10 strategic technology trends, which were unveiled at Gartner’s annual IT Symposium/XPO in Orlando.

To make generative AI tools (genAI) work as well as possible, tech companies have chosen to train their large language models (LLMs) on large amounts of text, even though doing so could run afoul of copyright laws.
Most recently, book publisher Penguin Random House has chosen to include a warning in its books stating the content may not be used or reproduced for the purpose of training AI models. And, according to The Bookseller, the AI warning will not only be added to new books but also to reprints of older titles.
The move is likely to spur more publishers to follow suit with similar warnings to their books.

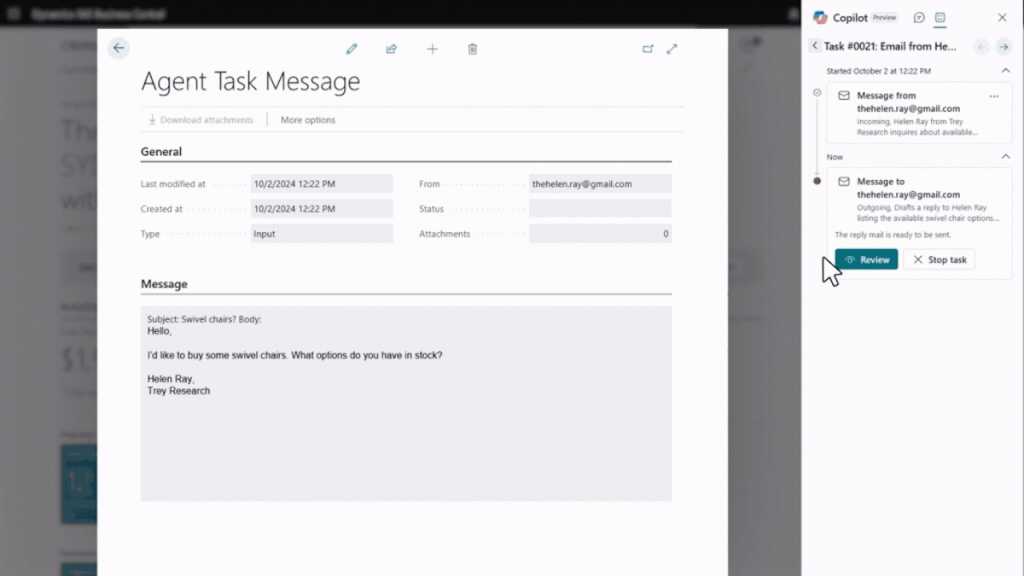
Microsoft will soon let customers build autonomous AI agents that can be configured to perform complex tasks with little or no input from humans.
Microsoft on Monday announced that tools to build AI agents in Copilot Studio will be available in a public beta that begins at the company’s Ignite conference on Nov. 19, with pre-built agents rolling out to Dynamics 365 apps in the coming month,s too.
Microsoft first unveiled plans to let users create AI agents in Copilot Studio — its low- or no-code AI development platform — in May with a private preview for select customers.
Generative AI (genAI) agents can be seen as the next stage in the evolution of conversational AI assistants such as Microsoft’s Copilot and OpenAI’s ChatGPT. While AI assistants respond directly to a user’s instructions — such as drafting an email or summarizing a document — autonomous AI agents are triggered by events and can perform more complex, multi-step processes on their own.
For example, a business could configure an AI agent to respond to the arrival of a customer email. At this point, the AI agent can look up the sender’s account details, check for past communications, and then take a range of actions — such as checking inventory or asking the customer for preferences — on its own.
There are a wide range of potential use cases, according to Microsoft, with the ability to tailor AI agents to a variety of tasks, from employee onboarding to supply chain automation.
“We think of agents as the new apps for an AI-powered world,” said Bryan Goode, corporate vice president for business Applications at Microsoft.
AI agents can be created via a no-code graphical interface in Copilot Studio, meaning no software development is required, according to Microsoft. Agents can then be published and accessed in a variety of places: from Microsoft’s Copilot AI assistant, on a website, or within an app.
The new Copilot AI agents can help take sales orders, for exaample.
Microsoft
Goode sees a broad appeal for workers outside of developers and IT: “We think everyone will need to be able to create agents in the future, much like how everyone can create spreadsheets or presentations in Microsoft 365,” he said.
“Agents really represent the democratization of AI for many enterprise users who have specific tasks they want to accomplish, but have no desire to become AI experts,” said Jack Gold, principal analyst with business consultancy J. Gold Associates.
Microsoft has taken steps to mitigate the impact of “hallucinations” –—a problem that’s exacerbated when AI agents can act independently and are given access to business applications.
For example, agents created for Dynamics will require human approval before carrying out certain actions, said Goode, such as preparing outbound communications. A viewable record of actions taken by an AI agent and why it took a decision is also kept in Copilot Studio.
More generally, Goode pointed to improvements to Microsoft’s Azure Content Safety system, which helps “measure, detect and mitigate hallucinations” more effectively, he said.
Nevertheless, hallucinations will continue to be a consideration for businesses that deploy AI agents, said Rowan Curran, senior analyst at Forrester.
“Buyers are rightly excited about the potential of agentic AI systems, but the reality of implementation is going to be just as challenging, if not more so, than the current generation of advanced RAG [retrieval-augmented generation] systems,” Curran said. “Having a strong data foundation will be essential for building useful AI agents: data quality and management aren’t problems that can be swept under the rug.”
Microsoft is developing 10 pre-configured AI agents for its Dynamics 365 business application suite. These include a “sales qualification agent” for Dynamics 365 Sales, a “sales order agent” for Dynamics 365 Business Central, and a “case management agent” Dynamics 365 Customer Service. The AI agents for Dynamics 365 will be available “over the coming months,” a Microsoft spokesperson said, with pricing and licensing details to be announced closer to the general availability launch.
Microsoft is not alone in building AI agents into its products: other business software vendors are doing the same, from Salesforce, which unveiled its Agentforce platform last month, to SAP and ServiceNow, as well as digital work app vendors such as Atlassian and Asana.
“In the next couple of years, you’ll see virtually all enterprise solutions providers deploy agents into their apps,” said Gold.

Apple was behind on smartphones, until it wasn’t. It lagged the crowd in digital music players, until it didn’t. There was a time when it was woeful on wearables, until it that changed. It’s the same old story when it comes to Apple Intelligence, which critics say lags behind the industry; eventually, it won’t.
Think back a little longer than the Overton-allotted three news-cycles we are allowed to recollect these days, and you’ll see that in each of the above examples, Apple didn’t go for the industry jugular until it had a solution that did the job. The iPhone wasn’t Apple’s first phone; the iPod wasn’t the first excursion into music (pre-digital Apple had the Apple CD SC in ’87); and much in mobile harkens to the iconic Apple Newton (including Apple Intelligence).
Do bang the drumBut success is about hitting the drums when the audience is most prepared to dance to the beat. And while some of the most vocal AI proponents on social media seem to think the technology is going to save the world, the vast majority of humans haven’t quite begun tapping toes to this tune.
Hundreds of millions of people (i.e. humanity) who fear for their way of life, employment prospects, and the effort they’ve invested in their own and their children’s education may be threatened by AI, so they’re less enthused about the arrival of this new tech. They want to adopt these AI toys slowly and deliberately and aren’t at all inclined to move fast and break things — because they know, in essence, they are the “things” that will be broke.
Like any good DJ, you have to read the floor. With that in mind, perhaps it matters less that Apple is allegedly behind some of its starry-eyed AI competitors? ChatGPT being 25% more accurate than Siri today might be a challenge, but it can be overcome.
Perhaps it’s actually best for Cupertino to move slowly with cool tools while letting others run headlong into regulation, litigation, and rejection by a humans that no longer believe technology can save us.
What do they want?While it is arguable that Apple’s high-risk strategy to market its new devices primarily on their capacity to run a tech that isn’t even shipping yet could be the equivalent of playing Milli Vanilli at a Taylor Swift party, Apple’s history shows it often plays the tunes its audience doesn’t even know its hungry to hear. So, what does the audience want?
More specifically, what doesn’t it want to hear (other than Milli Vanilli)?
A recent Stagwell National Research group survey tells us:
31% of Americans are concerned that there is too much AI-generated content on social media. 30% of people fret that AI might make decisions without consent. 30% are concerned about the impact of AI on personal data and privacy. 28% are worried AI makes it easier to spread misinformation. 27% think AI will be used and abused by criminals and fraudsters. 75% of people think apps should tell us when they use AI. 28% of users are put off by ads for smartphones with AI. 60% of smartphone users have already used an AI solution Men are more likely to purchase an AI smartphone than women.There’s lots of other insights, and all of them challenge the gold rush toward wholesale adoption of AI tech in daily life. Consumers want this rush to be led by a credible company.
They want a guide they can trust. Maybe Apple is that guide?
A guide to trust in AIThe company’s years-long commitments to security and privacy, and its decades of high consumer satisfaction mean it has that ethos — that credibility — to help guide the mass market to a more trusting embrace of AI. Apple has achieved this before — consider how global mobile payment leader Apple Pay managed to build trust even though many were suspicious of digital money when it was introduced.
It is the same when it comes to AI. People will resist being rushed at breakneck speed to an uncertain future led by unaccountable billionaire’s making nebulous “commitments” to some undefined “responsible” AI. They want the tech to also deliver trust.
Maybe that need for trust is why OpenAI agreed not to gather user data in order to win Apple’s Apple Intelligence integration deal? Perhaps Apple’s decision to create a circle of trust within which AI can be used while delivering highly specific services where it thinks it can make a difference matches the mood music people are hungry for. At Apple’s core, the fighter still remains. Let’s hope it does not squander consumer resistance on pockets full of mumbled promises.
Please follow me on LinkedIn, Mastodon, or join me in the AppleHolic’s bar & grill group on MeWe.

A new report from Secureworks shows that the North Korean group Nickel Tapestry has expanded its operations from getting North Korean IT workers illegally employed by companies in other countries to allowing the workers to steal data that can be used for extortion if they’re fired, according to The Register.
To avoid falling victim to such scams, companies are being warned to conduct a thorough screening of their job applicants — preferably with on-site interviews. It’s also a good idea to keep an eye on security involving remote access.
Warning signs to look out for include the use of Chrome Remote Desktop and AnyDesk software, if these are not part of the company’s regular equipment, and connections to Astrill VPN IP addresses. North Korean IT workers also tend to be reluctant to make video calls and often claim that their webcam is not working. However, according to Secureworks, they apparently have started experimenting with new software to handle video calls in the future.

Microsoft Office — best known for its Word, Excel, PowerPoint, and Outlook productivity applications — is how billions of people around the world work and study, whether they do it from home, an office, a classroom, or a combination of those. This suite of productivity tools is used by people working in more than 100 languages in nearly every country in the world, and it’s available in versions for personal, small business, enterprise, and educational use.
But there is more than one way to buy Office — or, rather, to buy the license to use it. There’s the “perpetual” version of Office that’s available as a one-time purchase: the current version is Office 2024. Then there’s the subscription version: originally called Office 365, Microsoft 365 plans are available in both personal and business subscriptions. At the enterprise level, both Microsoft 365 and Office 365 plans are available.
Microsoft has left no doubt: it wants you to use Microsoft 365, its cloud productivity platform. However, it also realizes that not all of its customers want to or can move to the cloud. For that reason, the company recently announced the release of Office 2024, almost apologetically:
Microsoft 365 is the best way to access the latest versions of the productivity apps that millions of people use every day to bring their ideas to life and power through tasks. But we know some of our customers still prefer a non-subscription way to access our familiar apps, which is why we’re releasing Office 2024 on October 1.
Available in consumer and small-business editions, this one-time purchase includes desktop versions of the core Office applications for a single Windows PC or Mac. For companies with more than five users, Microsoft offers Office LTSC 2024 to cater to organizations prioritizing an on-premises model. Office 2024 lacks many of the collaborative and cloud-powered features of Microsoft 365 apps, and its “locked-in-time” status means you won’t receive any new application features, just bug fixes and security updates.
Why choose to buy it one way and not the other? The answer can be complicated, especially because each suite of tools includes the same core applications, give or take. Here’s help deciding which version of Office is right for you or your company.
In this article: Office 2024 vs. Microsoft 365: Plans and pricing Office 2024 vs. Microsoft 365: Payment and licensing Office 2024 vs. Microsoft 365: Servicing Office 2024 vs. Microsoft 365: Do you want Microsoft to be your copilot? Office 2024 vs. Microsoft 365: Why your internet connection matters Office 2024 vs. Microsoft 365: Key questions to ask Office 2024 vs. Microsoft 365: Plans and pricing For personal use Office Home 2024: $150, one-time purchase for use on one computer; includes Word, Excel, PowerPoint, and OneNote for Windows or macOS. Microsoft 365 Personal: $70 a year or $7 a month (1 user, 5 devices); includes Word, Excel, PowerPoint, OneNote, Outlook, Teams, Editor, Clipchamp, Access*, Publisher*, Microsoft Defender, and OneDrive with 1TB cloud storage; apps available for Windows, macOS, Android, iOS, and web. Microsoft Copilot Pro is available as an add-on. Microsoft 365 Family: $100 a year or $10 a month (6 users, 5 devices each); includes Word, Excel, PowerPoint, OneNote, Outlook, Teams, Editor, Clipchamp, Access*, Publisher*, Microsoft Defender, and OneDrive with 1TB cloud storage per user; apps available for Windows, macOS, Android, iOS, and web. Microsoft Copilot Pro is available as an add-on.* Access and Publisher are available as Windows apps only; support for Publisher ends in 2026.
For small businesses Office Home & Business 2024: $250, one-time purchase for use on one computer; includes Word, Excel, PowerPoint, OneNote, and Outlook. Microsoft 365 Apps for business: $99/user/year or $10/user/month (up to 300 users, 5 devices per user); includes Word, Excel, PowerPoint, Outlook, and OneDrive with 1TB cloud storage per user. Microsoft 365 Copilot is available as an add-on. Microsoft 365 Business Basic, Standard, and Premium: plans range from $72/user/year to $264/user/year (up to 300 users); tools included depend on the level of your subscription. Desktop versions of Word, Excel, and other Office apps (installable on 5 devices per user) require a Standard plan or higher; the Basic plan offers only web and mobile versions. All plans include Exchange email hosting, Teams, SharePoint, and OneDrive with 1TB cloud storage per user. The Premium plan adds advanced security and management features. Microsoft 365 Copilot is available as an add-on. For enterprises Office LTSC Standard 2024 and Professional Plus 2024: available only through volume licensing; contact Microsoft for pricing. LTSC stands for Long Term Servicing Channel; according to Microsoft, it’s designed for regulated devices that can’t accept updates for security reasons and for systems that don’t connect to the internet. (Note, however, that it’s the only nonsubscription version of Office available for large organizations.) The Standard edition includes Word, Excel, PowerPoint, Outlook, and OneNote for Windows or macOS (1 device per user); Professional Plus adds Access.* Teams is not included but is available as a separate download. Microsoft 365 Apps for enterprise: $144/user/year (5 devices per user); includes Word, Excel, PowerPoint, Outlook, OneNote, Access*, Publisher*, and OneDrive with 1TB cloud storage per user. Teams and Microsoft 365 Copilot are available as add-ons. Office 365 E1, E3, and E5: plans range from $93/user/year to $429/user/year; apps included depend on the level of your subscription. Desktop versions of Word, Excel, and other Office apps require an E3 plan or higher; the E1 plan offers only web and mobile versions. All plans include Exchange email hosting, SharePoint, and OneDrive with 1TB cloud storage per user. The E3 plan offers up to 5TB of storage per user, and the E5 plan adds advanced security and management features. Teams and Microsoft 365 Copilot are available as add-ons. Microsoft 365 E3 and E5: plans range from $405/user/year to $657/user/year; these plans offer most of the same features as the Office 365 E3 and E5 plans, and also include Windows and additional Microsoft apps such as Visio, Loop, and Clipchamp. Teams and Microsoft 365 Copilot are available as add-ons. Other plans: Microsoft offers additional Microsoft 365 plans for education, government, and nonprofit organizations and for frontline workers.* Access and Publisher are available as Windows apps only; support for Publisher ends in 2026.
srcset=”https://b2b-contenthub.com/wp-content/uploads/2024/10/m365-vs-office-2024-at-a-glance.png?quality=50&strip=all 2390w, https://b2b-contenthub.com/wp-content/uploads/2024/10/m365-vs-office-2024-at-a-glance.png?resize=243%2C300&quality=50&strip=all 243w, https://b2b-contenthub.com/wp-content/uploads/2024/10/m365-vs-office-2024-at-a-glance.png?resize=768%2C947&quality=50&strip=all 768w, https://b2b-contenthub.com/wp-content/uploads/2024/10/m365-vs-office-2024-at-a-glance.png?resize=830%2C1024&quality=50&strip=all 830w, https://b2b-contenthub.com/wp-content/uploads/2024/10/m365-vs-office-2024-at-a-glance.png?resize=1245%2C1536&quality=50&strip=all 1245w, https://b2b-contenthub.com/wp-content/uploads/2024/10/m365-vs-office-2024-at-a-glance.png?resize=1660%2C2048&quality=50&strip=all 1660w, https://b2b-contenthub.com/wp-content/uploads/2024/10/m365-vs-office-2024-at-a-glance.png?resize=565%2C697&quality=50&strip=all 565w, https://b2b-contenthub.com/wp-content/uploads/2024/10/m365-vs-office-2024-at-a-glance.png?resize=136%2C168&quality=50&strip=all 136w, https://b2b-contenthub.com/wp-content/uploads/2024/10/m365-vs-office-2024-at-a-glance.png?resize=68%2C84&quality=50&strip=all 68w, https://b2b-contenthub.com/wp-content/uploads/2024/10/m365-vs-office-2024-at-a-glance.png?resize=389%2C480&quality=50&strip=all 389w, https://b2b-contenthub.com/wp-content/uploads/2024/10/m365-vs-office-2024-at-a-glance.png?resize=292%2C360&quality=50&strip=all 292w, https://b2b-contenthub.com/wp-content/uploads/2024/10/m365-vs-office-2024-at-a-glance.png?resize=203%2C250&quality=50&strip=all 203w” width=”1024″ height=”1263″ sizes=”(max-width: 1024px) 100vw, 1024px”>IDG
Office 2024 vs. Microsoft 365: Payment and licensingOne big difference between the Office 2024 and Microsoft 365 options is how you pay for them. If you are buying a “perpetual license” (such as with Office Home & Business 2024 or Office LTSC 2024), you pay a larger sum up front than with the subscription’s offerings under the Microsoft 365 brand, but you do so only once. When you subscribe to any of the Microsoft 365 plans, you pay annually or monthly for as long as you use the product.
Office 2024: A perpetual licenseWhether you buy a single copy of Office 2024 or download hundreds of seats via volume licensing, Microsoft calls this is a “one-time purchase” because you pay only once, not every month. Labels like “perpetual” technically note the type of license rather than payment methodology, but in this case, the kind of license is tied to whether it was bought outright or simply “rented.”
Microsoft defines the term as when “…you pay a single, up-front cost to get Office applications for one computer.” Up-front is the key adjective there. You have to ante up the entire purchase price before you get the software.
That purchase of a license to legally run the software gives you the right to use that version of Office 2024 in perpetuity. In other words, the license has no expiration date, and you may run the suite for as long as you want. Pay for Office 2024 this year and use it for as long as you’d like.
The gotcha is that if you want new features that come out with the next update, you will have to pay full price again when the next version comes out. There are no upgrade options on the perpetual license packages.
Microsoft 365: Office as a serviceMicrosoft 365 is a subscription service, the purchase method Microsoft would prefer you choose, where you pay the software giant monthly or annually. There is a discount, sometimes a tempting one, for going with the annual payment plan over the monthly one. (All enterprise plans require an annual commitment.) And the company is always sweetening this pot by offering more apps than you get with the perpetual license products and with a continuous supply of new features.
[ Related: Google Workspace vs. Microsoft 365: What’s the best office suite for business? ]
Like any subscription, Microsoft 365 provides a service — in this case, the right to run the suite’s applications and access the associated services — only as long as you continue to pay. Stop paying, and rights to run the apps expire. This happens in a progressive way, giving you time to download your data or update your payment plan, whichever you choose.
For 30 days after nonpayment, your plan will be “Expired.” You will still have access to all your apps and files. If you don’t activate it again while it’s in the Expired stage, it moves to “Disabled,” where it will stay for 90 days. You won’t be able to access your apps or data until you pay up. If you still don’t pay for your plan, it will be “Deleted.” At that point, it’s gone.
A Microsoft 365 license, then, is contingent on sustained payments. Halt the latter, and the license is revoked. Restart the payments — but don’t wait too long — to restore the license.
Office 2024 vs. Microsoft 365: ServicingAlthough payments define one difference between Office 2024 and Microsoft 365, Microsoft’s development and release pace is ultimately more important to users — and the IT professionals who support them.
Think of Office 2024 as traditional software — a bundle of tools that typically don’t change much until the next major version. That holds for servicing, too. Microsoft does release monthly security and quality updates for the perpetual license versions of Office. (You can check from within any Office app if there are updates available. From, say, a Word document, go to File > Account and look for Product Information. Then choose Update Options > Update Now.)
But Office 2024 doesn’t get the continually upgraded features and functionality that Microsoft 365 does. Feature-wise, what you get when you buy the suite is it. If you want the updates, at some point in the future, you will have to buy whatever version Microsoft is selling as a perpetual license then.
Microsoft regularly releases feature and security updates for Microsoft 365 apps, though. And it releases them as they happen. As new features and functionality accrete, and the applications in Microsoft 365 evolve, Microsoft will decide it’s time for a new version of Office. It will then package some of those features into an upgraded suite for customers who continue to make one-time, up-front purchases. How long they keep doing this likely depends on how long there is a demand for these locked-in-time versions.
[ Related: Microsoft 365: A guide to the updates ]
One other important note: Office 2024 and Office LTSC 2024 will be supported with security updates only through October 9, 2029. That’s just five years of support, down from seven years in Office 2019 and 10 years in prior releases. In contrast, with Microsoft 365 subscriptions, support never runs out — as long as you keep paying, of course.
Office 2024 vs. Microsoft 365: Do you want Microsoft to be your copilot?Microsoft also recently released Microsoft 365 Copilot, which Microsoft 365 business and enterprise subscribers can add for an additional $30 per user per month. The AI-powered productivity assistant is designed to enhance Word, Outlook, PowerPoint, Excel, Teams, and other Microsoft 365 applications, using large language models (LLMs) to understand your prompts, generate content, and assist with tasks. There’s also Copilot Pro, which brings many of the same features to Microsoft 365 consumer accounts for an extra $20 per month.
Key features include the following:
Natural-language prompts: You can communicate with Copilot in plain language. Content generation and task automation: Copilot can help you create content, such as emails, documents, presentations, and code, as well as automate repetitive tasks. Data analysis: Copilot can analyze data and provide insights to help you make informed decisions.Neither Microsoft 365 Copilot nor Copilot Pro is available without a Microsoft 365 subscription, though — so if you want Copilot integration with your Office apps, Office 2024 won’t get you there.
Office 2024 vs. Microsoft 365: Why your internet connection mattersOne reason to choose Office 2024 over Microsoft 365 is internet access, or lack of it. If you don’t have reliable access to the cloud, can’t be connected to the internet for security reasons, or — for whatever reason — your computer is often offline, this is the type of software you need.
In fact, internet access is one of the main reasons Microsoft can’t force everyone to subscribe to Microsoft 365. Microsoft 365 runs in apps that are downloaded to your computer, phone, or tablet, but those apps require near-constant internet access, especially if you use OneDrive and store your files in the cloud.
In standard use, Microsoft 365 may stop working if it can’t connect to the internet, depending on the features you’re using and the availability of offline capabilities within those applications. For some use cases, this is a deal breaker. However, Microsoft is looking to address that concern. Extended offline access allows devices with Microsoft 365 Apps for enterprise to remain active for up to six months without internet connectivity.
Office 2024, on the other hand, does not rely as heavily on an internet connection to operate, save files, and self-update. You can connect it when you have access and work offline when you don’t. This, as much as cost and a desire to stick to old-school software distribution models, is, perhaps, the most compelling reason to insist on one of the perpetual license products.
Office 2024 vs. Microsoft 365: Key questions to askIf you aren’t sure which version and pricing model is for you and your company, here are a few questions to ask yourself and your team:
Budget and pricing: How much are you willing to spend up front? What is a more attractive pricing model: a one-time expense or a recurring monthly or annual fee? What cost-saving options, such as volume licensing, are available?
Features and functionality: What specific features and applications do you need, and do you require specialized tools or integrations?
Deployment and management: Do you prefer cloud-based for its agility or on-premises deployment, perhaps for compliance reasons? Do you have IT resources to manage on-premises installations?
Collaboration and teamwork: How important is real-time collaboration? Do you need features like shared workspaces, online meetings, and file sharing?
Security and compliance: What are your organization’s security and compliance requirements? Does the delivery option you’re considering provide the necessary security features and certifications?
Updates and support: How often do you want to receive updates and new features, and do you need ongoing technical support?
Future-proofing: How do you envision your organization’s technology needs evolving? Does a subscription-based model provide the flexibility you need, or are you more concerned with ensuring stability in the coming months and years? Do you want to get a jump on generative AI features embedded in your productivity apps?
Whichever license you ultimately choose, you will get many of the same tools. And the reasons for making one choice over another may have less to do with price and features than with how you or your users work, support and security needs, reliability of internet access, online storage and collaboration needs, and how excited (or annoyed) you or your users are likely to be by new features that turn up, like a gift, in the software.
Choosing between a Microsoft 365 subscription and Office LTSC 2024 depends on your organization’s specific needs. For those seeking a dynamic, cloud-powered workspace with real-time collaboration and advanced features, Microsoft 365 offers a compelling solution. However, if on-premises stability and a single purchase model are paramount, Office LTSC may be the better fit. Consider your organization’s future-proofing needs and collaboration requirements when making this critical decision.
This article was originally published in July 2017 and most recently updated in October 2024.

Windows 11 24H2 has been released, but behind the scenes, Microsoft is constantly working to improve the newest version of Windows. The company frequently rolls out public preview builds to members of its Windows Insider Program, allowing them to test out — and even help shape — upcoming features.
The Windows Insider program is divided into four channels:
The Canary Channel is where platform changes (such as major updates to the Windows kernel and new APIs) are previewed. These changes are not tied to a particular Windows release and may never ship at all. Little documentation is provided, and builds are likely to be very unstable. This channel is best for highly technical users. The Dev Channel is where new features are introduced for initial testing, regardless of which Windows release they’ll eventually end up in. This channel is best for technical users and developers and builds in it may be unstable and buggy. In the Beta Channel, you’ll get more polished features that will be deployed in the next major Windows release. This channel is best for early adopters, and Microsoft says your feedback in this channel will have the most impact. The Release Preview Channel typically doesn’t see action until shortly before a new feature update is rolled out. It’s meant for final testing of an upcoming release and is best for those who want the most stable builds.The Beta and Release Preview Channels also receive bug-fix builds for the currently shipping version of Windows 11. See “How to preview and deploy Windows 10 and 11 updates” for more details about the four channels and how to switch to a different channel.
Not everyone can participate in the Windows 11 Insider program, because the new operating system has more stringent system requirements than Windows 10. If your PC fails to meet the minimum hardware requirements for Windows 11, you cannot join the Windows 11 Insider Program. (See “How to check if your PC can run Windows 11.”)
Below you’ll find information about the Windows 11 preview builds that have been announced by Microsoft in the past six months. (For the Release Preview Channel, we cover builds released for the current version of Windows 11, not for earlier versions.) For each build, we’ve included the date of its release, which Insider channel it was released to, a summary of what’s in the build, and a link to Microsoft’s announcement about it.
Note: If you’re looking for information about updates being rolled out to all Windows 11 users, not previews for Windows Insiders, see “Windows 11: A guide to the updates.”
The latest Windows 11 Insider preview builds Windows 11 Insider Preview Build 22635.4371Release date: October 18, 2024
Released to: Beta Channel
In this build, those in the Beta Channel who have turned the toggle on to receive the latest updates as soon as they are available can now use the new Narrator key + Ctrl + X shortcut to copy what Narrator last spoke to clipboard. It follows the pattern of using Narrator key + X, which repeats the last spoken phrase out loud.
Those who have turned the toggle on to receive the latest updates as soon as possible get several fixes for several bugs, including one in which Narrator would slow down after 15 minutes of continuous use with a single application.
An update for the Snipping Tool (version 11.2409.23.0 and newer) is also being rolled out to Windows Insiders in the Beta and Release Preview Channels. It introduces a new “Copy as table” feature.
(Get more info about Windows 11 Insider Preview Build 22635.4371.)
Windows 11 Insider Preview Build 26120.2130Release date: October 18, 2024
Released to: Dev Channel
In this build, those in the Dev Channel who have turned the toggle on to receive the latest updates get several new features, including one in which “All apps” is now just “All” on the Start menu.
Those in the Dev Channel who have turned the toggle on to receive the latest updates also get several bug fixes, including for a bug in which clipboard history did not display items you had copied.
There are two known issues in this build, including one in which if you click or tap on a letter on Start menu’s All apps list, the All apps list may break. If you encounter this issue, try rebooting or restarting explorer.exe to fix it.
(Get more info about Windows 11 Insider Preview Build 26120.2130.)
Windows 11 Insider Preview Build 27729Release date: October 17, 2024
Released to: Canary Channel
This build adds the ability to configure the Copilot key. You can choose to have the Copilot key launch an app that is MSIX packaged and signed, thus indicating the app meets security and privacy requirements to keep customers safe.
The build also fixes a variety of bugs, including one in which the screen went black for a few seconds for some people when using Alt + Tab.
There are five known issues in this build, including one in which some Insiders with PCs that have older NVIDIA GPUs (like the GTX 970, Quadro K620, etc.) are experiencing some issues where their displays appear stuck at a black screen and unresponsive or seeing their GPUs showing errors in Device Manager and not working correctly.
(Get more info about Windows 11 Insider Preview Build 27729.)
Windows 11 Insider Preview Build 22635.4367Release date: October 11, 2024
Released to: Beta Channel
In this build, those in the Beta Channel who have turned the toggle on to receive the latest updates as soon as they are available get a small set of general improvements and fixes that Microsoft claims improves the overall experience of running Windows. They also now have the ability to share directly to apps that support sharing in Windows when right-clicking on local files in File Explorer or the desktop.
Those who have turned the toggle on to receive the latest updates as soon as possible get several bug fixes, including for one in which some Insiders saw an unexpected amount of spacing between items in the Start menu All Apps list.
(Get more info about Windows 11 Insider Preview Build 22635.4367.)
Windows 11 Insider Preview Build 26120.2122Release date: October 11, 2024
Released to: Dev Channel
In this build, those in the Dev Channel who have turned the toggle on to receive the latest updates get a small set of general fixes that Microsoft says improve the overall experience of running Windows. The Disconnect and Logoff dialogs in Task Manager now support dark mode and text scaling.
Those in the Dev Channel who have turned the toggle on to receive the latest updates also get one bug fix, for a bug that caused the screen to go black for a few seconds for some people when using Alt + Tab.
Everyone in the Dev Channel gets several bugs fixed, including one in which some Insiders saw error 0x800f0825 when trying to install the latest Dev Channel builds.
There are two known issues in this build, including one in which if you click or tap on a letter on Start menu’s All apps list, the All apps list may break. If you encounter this issue, try rebooting or restarting explorer.exe to fix it.
(Get more info about Windows 11 Insider Preview Build 26120.2122.)
Windows 11 Insider Preview Build 26100.2152Release date: October 10, 2024
Released to: Release Preview Channel
This build gradually rolls out a number of new features, including one in which you can stop the suggestions to turn off notifications from certain apps. Select the ellipses (…) in the notification and turn it off. You can also go to Settings > System > Notifications and turn it off from there.
The build also immediately rolls out a change in which you can configure the Copilot key on the keyboard. The build also immediately fixes a number of bugs, including one in which you could not sign in to your account from the web because the screen stopped responding.
(Get more info about Windows 11 Insider Preview Build 26100.2152.)
Windows 11 Insider Preview Build 27723Release date: October 9, 2024
Released to: Canary Channel
This build introduces several minor changes and features, including one in which you can share local files directly from within the search results shown in the search box on the taskbar.
There are five known issues in this build, including one for those using Copilot+ PCs, in which if you are joining the Canary Channel on a new Copilot+ PC from the Dev Channel, Release Preview Channel, or retail, you will lose your Windows Hello PIN and biometrics to sign into your PC. You should be able to re-create your PIN by clicking “Set up my PIN.”
(Get more info about Windows 11 Insider Preview Build 27723.)
Windows 11 Insider Preview Build 26120.1930Release date: October 4, 2024
Released to: Dev Channel
In this build, those in the Dev Channel who have turned the toggle on to receive the latest updates get a small set of general improvements and one bug fix, for a bug in which the boot menu wasn’t displaying correctly for some Insiders with dual-boot devices.
Everyone in the Dev Channel can now configure the Copilot key. You can have the Copilot key launch an app that is MSIX packaged and signed, increasing security and privacy.
There are two known issues in this build, including one in which if you click or tap on a letter on Start menu’s All apps list, the list may break. If you encounter this issue, please try rebooting or restarting explorer.exe to fix it.
(Get more info about Windows 11 Insider Preview Build 26120.1930.)
Windows 11 Insider Preview Build 22635.4300Release date: October 4, 2024
Released to: Beta Channel
In this build, those in the Beta Channel who have turned the toggle on to receive the latest updates as soon as they are available will see “All” instead of “All apps” on the Start menu. In addition, Windows Search runs IFilters in the Less Privileged App Containers (LPACs). LPACs are like app containers, but they deny even more permissions by default. The intent is that a process running in a LPAC has access only to the resources needed by it. This helps to minimize the potential damage that can be caused by a compromised process by limiting its access to sensitive system components and data.
Two bugs are fixed for those who have turned the toggle on to receive the latest updates as soon as possible, including one in which items in the navigation pane became very spread out for some people.
There are two known issues in the build, including one in which live captions will crash if you try to use them.
(Get more info about Windows 11 Insider Preview Build 22635.4300.)
Windows 11 Insider Preview Build 27718Release date: October 2, 2024
Released to: Canary Channel
This build introduces a number of minor new changes and features. You can now drag apps from the Pinned section of the Start menu and pin them to the taskbar. For laptops on battery, a notification will pop up asking you to plug in your laptop if the battery level reaches 20% while Energy Saver is set to “Always On.”
Several bugs have been fixed, including one in which the emoji panel closed when you tried to switch to the kaomoji and symbols sections, or after selecting an emoji, and another in which the Widgets icon sometimes unexpectedly displayed twice in the taskbar.
There are three known issues in this build, including one for those using Copilot+ PCs, in which If you are joining the Canary Channel from the Dev Channel, Release Preview Channel or retail, you will lose Windows Hello pin and biometrics to sign into your PC; you’ll see error 0xd0000225 and an error message “Something went wrong, and your PIN isn’t available.” You should be able to re-create your PIN by clicking “Set up my PIN.”
(Get more info about Windows 11 Insider Preview Build 27718.)
Windows 11 Insider Preview Build 26120.1912Release date: September 30, 2024
Released to: Dev Channel
In this build, those in the Dev Channel who’ve turned on the toggle to receive the latest updates get a small set of general improvements and fixes that Microsoft says improves the overall experience of running Windows. In addition, Windows Mobile Hotspot has been enhanced to support 6GHz connections. The new band requires chips that support the feature and updated drivers; not all chips that support 6GHz Wi-Fi in general will support the 6GHz mobile hotspot.
Those in the Dev Channel who agreed to receive the latest updates also get several bug fixes, including one in which Task Manager’s Settings page might have a white background when it should not.
There is one known issue in this build: if you click or tap on a letter on Start menu’s All apps list, the All apps list may break. If you encounter this issue, try rebooting or restarting explorer.exe to fix it.
(Get more info about Windows 11 Insider Preview Build 26120.1912.)
Windows 11 Insider Preview Build 22635.4291Release date: September 30, 2024
Released to: Beta Channel
In this build, those in the Beta Channel who have turned on the toggle to receive the latest updates as soon as they are available get an updated Task Manager design in which the Disconnect and Logoff dialogs in Task Manager now support dark mode and text scaling. They also get several bug fixes, including one in which explorer.exe crashed sporadically when using ALT + Tab in recent builds.
Everyone in the Beta Channel gets several bug fixes, including one in which Work Folders files failed to sync when Defender for Endpoint was on.
There are two known issues in the build, including one in which live captions will crash if you try to use them.
(Get more info about Windows 11 Insider Preview Build 22635.4291)
Windows 11 Insider Preview Build 26100.1876Release date: September 23, 2024
Released to: Release Preview Channel
This build, for those using Windows 11 version 24H2, gradually rolls out a number of new features, including one in which when your device’s battery power is running low, a pop-up window will appear that asks you to plug in your device. This occurs when the battery level reaches 20% and while Energy Saver is set to “Always On.
Several bug fixes are being immediately rolled out, including one in which when a combo box has input focus, a memory leak might have occurred when you closed that window.
(Get more info about Windows 11 Insider Preview Build 26100.1876.)
Windows 11 Insider Preview Builds 22621.4247 and 22631.4247Release date: September 23, 2024
Released to: Release Preview Channel
In this update for users on Windows 11 22H2 and 23H2, a variety of features are being rolled out slowly, including one in which the “Sign out” option is now on the account manager when you open the Start menu. To change to a different user, select the ellipses (…). A list of other users appears to make it easier to switch.
The update also fixes several bugs, including one in which Microsoft Edge sometimes stopped responding when you used IE mode.
(Get more info about Windows 11 Insider Preview Builds 22621.4247 and 22631.4247.)
Windows 11 Insider Preview Build 22635.4225Release date: September 20, 2024
Released to: Beta Channel
In this build, those in the Beta Channel who have turned the toggle on to receive the latest updates as soon as they are available will get the ability to share content to an Android device from the context menu in File Explorer and on the desktop. To use this feature, the Phone Link app must be installed and configured on your PC.
Those who have turned the toggle on to receive the latest updates as soon as possible get a fix for a bug in which the emoji panel didn’t work properly.
Everyone in the Beta Channel can now configure the Copilot key. You can choose to have the Copilot key launch an app that is MSIX packaged and signed, thus indicating the app meets security and privacy requirements.
Everyone in the Beta Channel gets several bug fixes, including for a bug in which some Insiders experienced a bug check when closing Notepad.
There is one known issue in the build, in which if you click or tap on a letter on the Start menu’s All apps list, the list may break. If you encounter this issue, try rebooting or restarting explorer.exe to fix it.
(Get more info about Windows 11 Insider Preview Build 22635.4225.)
Windows 11 Insider Preview Build 26120.1843Release date: September 20, 2024
Released to: Dev Channel
In this build, those in the Dev Channel who have turned the toggle on to receive the latest updates get a new feature, in which File Explorer provides you with quick access to files that have been shared with you. If you are signed into Windows with your Microsoft account or Entra ID account, you will be able to view files that have been shared with your account, such as email, Teams chat, etc. You can access this feature by launching File Explorer Home and clicking on the Shared tab.
Those in the Dev Channel who have turned the toggle on to receive the latest updates get several bug fixes, including one in which when pressing Windows key + E, a screen reader might unexpectedly say a pane had focus, or focus may not be set within File Explorer at all.
Everyone in the Dev Channel gets a number of bug fixes, including one in which could result in the Widgets icon unexpectedly displaying in the taskbar twice sometimes.
There are four known issues in this build, including one in which if you click or tap on a letter on Start menu’s All apps list, the list may break. If you encounter this issue, try rebooting or restarting explorer.exe to fix it.
(Get more info about Windows 11 Insider Preview Build 26120.1843.)
Windows 11 Insider Preview Build 22635.4145Release date: August 30, 2024
Released to: Beta Channel
In this build, those in the Beta Channel who have turned the toggle on to receive the latest updates as soon as they are available will see several new features, including one in which the Sign out option is immediately visible in the new account manager on the Start menu. There’s also a list of signed in users under the three-dot icon so it’s faster to switch accounts. The mouse and touchscreen controls have more options, and hotspots now appear on the desktop when users right-click the Windows Spotlight icon. The changes are being rolled out gradually.
Those who have turned the toggle on to receive the latest updates as soon as possible get fixes for several bugs, including one in which explorer.exe crashed when interacting with archive files. These fixes are being rolled out gradually
Everyone in the Beta Channel gets a number of bug fixes, including for a bug in which the [NetJoinLegacyAccountReuse] registry key has been removed.
There is one known issue in the build: if you click or tap on a letter on Start menu’s All apps list, the All apps list may break. If you encounter this issue, try rebooting or restarting explorer.exe to fix it.
(Get more info about Windows 11 Insider Preview Build 22635.4145.)
Windows 11 Insider Preview Build 27695Release date: August 30, 2024
Released to: Canary Channel
In this build, Windows Local Administrator Password Solution (LAPS) has been improved with a new ability to recover encrypted passwords from Active Directory (AD) backup media even when there are zero AD domain controllers running.
A number of bugs have been fixed, including one in which Ctrl + F would sometimes not start a search in File Explore, and another in which the colors in the Performance section of Task Manager weren’t displayed correctly in dark mode.
There are two known issues in this build, including one for those using Copilot+ PCs, in which If you are joining the Canary Channel on a new Copilot+ PC from the Dev Channel, Release Preview Channel or retail, you will lose your Windows Hello PIN and biometrics to sign into your PC with error 0xd0000225 and error message “Something went wrong, and your PIN isn’t available.” You should be able to re-create your PIN by clicking Set up my PIN.
(Get more info about Windows 11 Insider Preview Build 27695.)
Windows 11 Insider Preview Build 22635.4082Release date: August 26, 2024
Released to: Beta Channel
In this build, those in the Beta Channel who have turned the toggle on to receive the latest updates as soon as they are available will see the media controls at the lower bottom center of the Lock screen when media is being played. There is also now an option to turn off the suggestions to disable notifications from certain apps. These features are being rolled out gradually.
Those who have turned the toggle on to receive the latest updates as soon as possible get fixes for several bugs, including one in which explorer.exe crashed for some Insiders when closing apps from the taskbar. These fixes are being rolled out gradually.
Everyone in the beta channel gets one bug fix, in which the [NetJoinLegacyAccountReuse] registry key has been removed.
There are two known issues for everyone in the Beta Channel, including one that causes explorer.exe to crash when interacting with archive files.
(Get more info about Windows 11 Insider Preview Build 22635.4082.)
Windows 11 Insider Preview Builds 22621.4108 and 22631.4108Release date: August 19, 2024
Released to: Release Preview Channel (Windows 11 23H2 and 22H2)
Starting with this update, a variety of features will be rolled out slowly, including one that lets you share content to your Android device from the Windows Share window. To do this, you must pair your Android device to your Windows PC. Use the Link to Windows app on your Android device and Phone Link on your PC.
A number of bugs are being fixed, including one in which when a combo box has input focus, a memory leak might occur when you close that window.
(Get more info about Windows 11 Insider Preview Builds 22621.4108 and 22631.4108.)
Windows 11 Insider Preview Build 22610.1586Release date: August 19, 2024
Released to: Release Preview Channel (Windows 11 24H2)
This build, for those with Windows 11 version 24H2, gradually rolls out a new feature in which when you right-click a tab in File Explorer, you have the choice to duplicate it.
A wide variety of bug fixes are being gradually rolled out, including for a bug in which memory leak occurred when you interacted with archive folders and another in which File Explorer stopped responding when you browsed within it.
Three bug fixes have been immediately released to everyone, including one in which a deadlock occurred in the domain controller (DC) when it started up in the DNS client.
(Get more info about Windows 11 Insider Preview Build 26100.1586.)
Windows 11 Insider Preview Build 22635.4076Release date: August 19, 2024
Released to: Beta Channel
In this build, those in the Beta Channel who have turned the toggle on to receive the latest updates will find that a feature introduced in Build 22635.3930 that showed a Studio Effects icon in the system tray when using any application with a Studio Effects-enabled camera has temporarily been disabled. It will be re-enabled in a future build.
Those in the Beta Channel who have turned the toggle on to receive the latest updates get a variety of bug fixes, including for a bug in which Voice Access commands weren’t working for non-English supported languages.
A wide variety of bugs are fixed for everyone in the Beta Channel, including one in which Windows Backup sometimes failed in devices with an Extensible Firmware Interface (EFI) system partition (ESP).
There are two known issues for everyone in the Beta Channel, including one in which explorer.exe crashes when interacting with archive files.
(Get more info about Windows 11 Insider Preview Build 22635.4076.)
Windows 11 Insider Preview Build 26120.1542Release date: August 19, 2024
Released to: Dev Channel
In this build, those in the Dev Channel who have turned the toggle on to receive the latest updates get a new feature that adds first letter navigation support to the taskbar. When keyboard focus is set to the taskbar (WIN + T), you can press a letter, and it will jump to the open or pinned app whose name starts with that letter. The feature is being gradually rolled out so isn’t yet available to everyone.
Those in the Dev Channel who have turned the toggle on to receive the latest updates get fixes for three bugs, including one in which the emoji panel closed when trying to switch to the kaomoji and symbols sections, or after selecting an emoji.
Everyone in the Dev Channel gets a number of bug fixes, including for a bug in which adding languages or optional features might fail with error 0x800f081f.
There are two known issues in this build, including one in which navigating between different pages in Task Manager may crash it.
(Get more info about Windows 11 Insider Preview Build 26120.1542.)
Windows 11 Insider Preview Build 27686Release date: August 15, 2024
Released to: Canary Channel
This build includes the new Windows Sandbox Client Preview that is now updated via the Microsoft Store. It introduces runtime clipboard redirection, audio/video input control, and the ability to share folders with the host at runtime. You can access these via the new “…” icon at the upper right on the app. This preview also includes a very early version of command line support. (Commands may change over time.) You can use the wsb.exe –help command for more information.
The build also includes optimizations to improve battery life and a detach virtual hard disk (VHD/VHDx) button in Settings that makes it simpler to detach your VHD/VHDx as needed.
A number of bugs have been fixed, including one in which Dev Drive VHDs weren’t automatically remounting when the underlying volume was dismounted and brought back online, and one in the Windows Security app where if you browsed the networks under Firewall & Network protection, it showed a broken glyph (a rectangle) next to the network name rather than a network icon.
There are two known issues in this build, including one in which if you are joining the Canary Channel on a new Copilot+ PC from the Dev Channel, Release Preview Channel, or retail, you will lose Windows Hello PIN and biometrics to sign into your PC. You should be able to re-create your PIN by clicking “Set up my PIN.”
(Get more info about Windows 11 Insider Preview Build 27686.)
Windows 11 Insider Preview Build 26120.1350Release date: August 9, 2024
Released to: Dev Channel
In this build, those in the Dev Channel who have turned the toggle on to receive the latest updates can more easily share content to an Android device from Windows share window. The feature requires you to pair your Android device to your Windows PC using the Link to Windows app on Android and Phone Link on your PC. The feature is being rolled out gradually.
Those in the Dev Channel who have turned the toggle on to receive the latest updates get one fix that addresses an issue in which graphs on the Performance page in Task Manager did not show the correct colors when using dark mode again. The fix is being rolled out gradually.
Everyone in the Dev Channel gets several bug fixes, including for a bug in which Windows Sandbox failed to launch with error 0x80370106.
There are four known issues in this build, including one in which navigating between different pages in Task Manager may crash it.
(Get more info about Windows 11 Insider Preview Build 26120.1350.)
Windows 11 Insider Preview Build 22635.4010Release date: August 9, 2024
Released to: Beta Channel
In this build, many of those in the Beta Channel who have turned the toggle on to receive the latest updates will see the simplified system tray with shortened date/time change that began rolling out with Build 22635.3930. The feature is being rolled out gradually.
Those who have turned the toggle on to receive the latest updates get fixes for two bugs, one in which the dropdown at the top of the GPU section of Performance wasn’t showing in dark mode when dark mode was enabled, and the other in which if you pressed the Shift key when you right-clicked on an app icon on the taskbar, it opened another instance of the app rather than opening the expected menu.
There are three known issues for everyone in the Beta Channel, including one that causes explorer.exe to crash for some Insiders when closing apps from the taskbar.
(Get more info about Windows 11 Insider Preview Build 22635.4010.)
Windows 11 Insider Preview Build 26120.1340Release date: August 5, 2024
Released to: Dev Channel
In this build, those in the Dev Channel who have turned the toggle on to receive the latest updates get improvements for spelling and corrections in voice access, including the ability to dictate characters at a faster speed and have more editing flexibility with selection, deletion, and text navigation commands.
Those in the Dev Channel who have turned the toggle on to receive the latest updates get a fix for a bug in which items under “Let desktop apps access your location” section in Settings > Privacy & Security > Location had visibly flickered although there were no changes displayed.
There are four known issues in this build, including one in which navigating between different pages in Task Manager may crash it.
(Get more info about Windows 11 Insider Preview Build 26120.1340.)
Windows 11 Insider Preview Build 22635.4005Release date: August 2, 2024
Released to: Beta Channel
In this build, those in the Beta Channel who have turned the toggle on to receive the latest updates get a small set of general tweaks and fixes that Microsoft says improves the overall experience of running Windows.
Those who have turned the toggle on to receive the latest updates get one fix for a bug that caused sporadic explorer.exe crashes for some Insiders.
There are three known issues for everyone in the Beta Channel, including one that causes explorer.exe to crash for some Insiders when closing apps from the taskbar.
(Get more info about Windows 11 Insider Preview Build 22635.4005.)
Windows 11 Insider Preview Build 22635.4000Release date: July 26, 2024
Released to: Beta Channel
In this build, those in the Beta Channel who have turned the toggle on to receive the latest updates get a small set of general improvements and fixes, as well as some improvements to spelling and corrections in voice access.
Those who have turned the toggle on to receive the latest updates get two bug fixes, one in which Notification Center got stuck and would not open, and another that caused issues with launching the touch keyboard and emoji panel.
Everyone in the Beta Channel gets two fixes that address one bug in which Narrator would not work as expected when navigating through the Recent, Favorites, and Shared tab items, and another that caused the context menu in Home or Gallery to open in the wrong position when using Arabic or Hebrew display languages.
There are four known issues for everyone in the Beta Channel, including one in which files shared with you in File Explorer may not appear if there has been no interaction with that file.
(Get more info about Windows 11 Insider Preview Build 22635.4000.)
Windows 11 Insider Preview Build 26120.1330Release date: July 26, 2024
Released to: Dev Channel
In this build, those in the Dev Channel who have turned the toggle on to receive the latest updates can duplicate a tab by right-clicking on it in File Explorer. (Note: This is being gradually rolled out.)
Those in the Dev Channel who have turned the toggle on to receive the latest updates get a fix for a bug in which no text appeared on the Windows Update page in Settings for Insiders using certain languages.
There are three known issues in this build, including one in which the BitLocker Recovery screen issue documented here may also impact Windows Insiders in the Dev Channel.
(Get more info about Windows 11 Insider Preview Build 26120.1330.)
Windows 11 Insider Preview Build 26100.1297Release date: July 25, 2024
Released to: Release Preview Channel
This build, for those with Windows 11 version 24H2, gradually rolls out a wide variety of new features, including pinning apps to the taskbar by dragging and dropping items directly to taskbar from the pinned section in the Start menu, using your mouse to drag files between breadcrumbs in the File Explorer address bar, and directly sharing to specific Microsoft Teams channels and group chats in the Windows share window.
It also includes a variety of changes released immediately to everyone, including being able to use OneDrive as a RemoteApp in Azure Virtual Desktop.
(Get more info about Windows 11 Insider Preview Build 26100.1297.)
Windows 11 Insider Preview Build 26257Release date: July 24, 2024
Released to: Canary Channel
This build introduces the ability to duplicate a tab by right-clicking it in File Explorer. In addition, if you use the netsh wlan show networks command, you should be able to read SSIDs that are UTF-8 encoded. This means that Wi-Fi SSIDs with Unicode characters (like emojis) should be properly displayed in netsh output. This change is just beginning to roll out, so not all Insiders in the Canary Channel will see it right away.
Several bugs have been fixed, including one in which the address bar dropdown appeared unexpectedly while you were using File Explorer.
There are three known issues in this build, including one in which some Windows Insiders in the Canary and Dev Channels are stuck on Build 26040 or Build 23620.
(Get more info about Windows 11 Insider Preview Build 26257.)
Windows 11 Insider Preview Build 22635.3936Release date: July 22, 2024
Released to: Beta Channel
In this build, those in the Beta Channel who have turned the toggle on to receive the latest updates will see updated designs for the “Open with” dialog where the group headers are removed, among a few other changes.
Those who have turned the toggle on to receive the latest updates get several bug fixes, including one in which text suggestions for the hardware keyboard did not work.
Note that the bug fixes and new features are being gradually rolled out.
There are nine known issues for everyone in the Beta Channel, including one in which swipe invocation for Widgets may not work if the taskbar is center-aligned instead of left-aligned.
(Get more info about Windows 11 Insider Preview Build 22635.3936.)
Windows 11 Insider Preview Build 26120.1252Release date: July 15, 2024
Released to: Dev Channel
In this build, those in the Dev Channel who have turned the toggle on to receive the latest updates can now pin apps from the Start menu to the taskbar by dragging and dropping items directly to taskbar from the pinned section in the Start menu.
Those in the Dev Channel who have turned the toggle on to receive the latest updates get several bug fixes, including one in which explorer.exe crashed when navigating away from Home.
Everyone in the Dev Channel gets a variety of bug fixes, including for one in which some Insiders saw a bug check with error KERNEL_SECURITY_CHECK_FAILURE, and another in which Settings > System > Power & Battery had duplicate text when showing a warning about a slow charger.
There are three known issues in this build, including one in which the Windows Update page in Settings is not displaying correctly for Insiders using certain languages (no text shows).
(Get more info about Windows 11 Insider Preview Build 26120.1252.)
Windows 11 Insider Preview Build 22635.3930Release date: July 12, 2024
Released to: Beta Channel
In this build for Windows 11 version 23H2, those in the Beta Channel who have turned the toggle on to receive the latest updates can get quick access to files that have been shared with you. If you are signed into Windows with your Microsoft account, you will be able to view files that have been shared with your account, such as email, Teams chat, etc. If you are a commercial customer who is signed in with your Microsoft Entra ID account, you will additionally be able to view files that they have shared with others. You can access this feature by launching File Explorer Home and clicking on the Shared tab item.
In addition, those in the Beta Channel who have turned the toggle on to receive the latest updates can access Studio Effects in Quick Settings from the system tray of the taskbar. Note that this is being gradually rolled out and so is not yet available to everyone.
Those who have turned the toggle on to receive the latest updates get several bug fixes, including for one in which the All apps list wasn’t being read out by screen readers.
Everyone in the Beta Channel gets one bug fix, in which you can now view or interact with the taskbar after you install KB5039302.
There are seven known issues for everyone in the Beta Channel, including one in which swipe invocation for Widgets may not work if taskbar is center-aligned instead of left-aligned.
(Get more info about Windows 11 Insider Preview Build 22635.3930.)
Windows 11 Insider Preview Builds 22621.3951 and 22631.3951Release date: July 11, 2024
Released to: Release Preview Channel
In this update, you can drag apps from the Pinned section of the menu and pin them to the taskbar, and when you right-click a tab in File Explorer, you have the choice to duplicate it. Note that these features and several others might not be available to all users because they will roll out gradually.
(Get more info about Windows 11 Insider Preview Builds 22621.3951 and 22631.3951.)
Windows 11 Insider Preview Build 26252Release date: July 10, 2024
Released to: Canary Channel
This build begins to roll out the “Weather and more” feature, which brings finance, traffic, and sports to your Lock screen, alongside weather information. You can also now pin apps from the Start menu to the taskbar by dragging and dropping items directly to taskbar from the pinned section in the Start menu.
Several bugs have been fixed, including one that caused colors in the Performance section of Task Manager to not display correctly in dark mode, and another in which Settings > System > Power & Battery had duplicate text when showing a warning about a slow charger.
There one known issue with this build, in which some Windows Insiders in the Canary and Dev Channels are stuck on Build 26040 or Build 23620.
(Get more info about Windows 11 Insider Preview Build 26252.)
Windows 11 Insider Preview Build 22635.3858Release date: June 28, 2024
Released to: Beta Channel
In this build, those in the Beta Channel who have turned the toggle on to receive the latest updates get some minor changes to simplify the Windows share window, including removing the search box. In addition, the preview thumbnail title in the taskbar, Alt + Tab, and Task View for File Explorer windows will now indicate if that window includes multiple tabs.
Those in the Beta Channel who have turned the toggle on to receive the latest updates get a number of bug fixes, including some addressing accessibility issues where File Explorer, Common File Dialog (CFD), and Browse/Shortcuts Dialogs did not respond appropriately to your text size / scaling preferences.
Everyone in the Beta Channel gets several bug fixes, including one in which the app icon flashing in the taskbar is now be a bit easier to see. Another fix addresses a bug in which Group Policy failed to detect when a network’s speed is slow, instead assuming that a fast link was present.
There are six known issues for everyone in the Beta Channel, including one in which swipe invocation for Widgets may not work if taskbar is center-aligned instead of left-aligned.
(Get more info about Windows 11 Insider Preview Build 22635.3858.)
Windows 11 Insider Preview Build 26244Release date: June 28, 2024
Released to: Canary Channel
This build includes a small set of general enhancements and fixes that improve the overall experience of running Windows, according to Microsoft. In addition, a new Game Pass recommendation card on the Settings homepage will be shown to you if you actively play games on your PC.
One bug was fixed, in which some Insiders saw a Pcasvc.dll error dialog pop-up with the message “Missing entry: PcaWallpaperAppDetect” after upgrading from Windows 11, version 22H2/23H2 to a 26xxx build.
There are two known issues with this build, one in which some Windows Insiders in the Canary and Dev Channels are stuck on Build 26040 or Build 23620, and another in which colors in the Performance section aren’t displaying correctly in dark mode.
(Get more info about Windows 11 Insider Preview Build 26244.)
Windows 11 Insider Preview Build 22635.3790Release date: June 21, 2024
Released to: Beta Channel
In this build for Windows 11, version 23H2, those in the Beta Channel who have turned the toggle on to receive the latest updates can use their mobile device directly from the Start menu. See this blog post for details.
Those who have turned the toggle on to receive the latest updates get one bug fix, which addresses contrast issues of certain elements in File Explorer (left navigation pane, view pane/folder view, status bar buttons on the bottom right) in light, dark, and high contrast themes.
Everyone in the Beta Channel gets two bug fixes, for a bug in which Settings was crashing when trying you were trying to look at Wi-Fi properties, and another in which Settings might crash when attempting to install an optional feature via Settings > System > Option features.
There are six known issues for everyone in the Beta Channel, including one in which swipe invocation for Widgets may not work if taskbar is center-aligned instead of left-aligned, and another in which some Insiders to see errors when attempting to use Voice Typing.
(Get more info about Windows 11 Insider Preview Build 22635.3790.)
Windows 11 Insider Preview Build 26100.994Release date: June 20, 2024
Released to: Release Preview Channel
This build, for those with Windows 11 version 24H2, fixes a variety of bugs, including one in which Windows Defender Application Control (WDAC) failed to verify the policies of some apps, and another that caused DWM.exe to stop responding.
(Get more info about Windows 11 Insider Preview Build 26100.994.)
Windows 11 Insider Preview Build 26241Release date: June 19, 2024
Released to: Canary Channel
This build includes a small set of general improvements and fixes that improve the overall experience of running Windows, according to Microsoft. In addition, dragging-and-dropping files between breadcrumbs is now available in the File Explorer Address Bar.
Several bugs have been fixed, including one that caused File Explorer to crash when going to Home.
There are two known issues with this build, one in which some Windows Insiders in the Canary and Dev Channels are stuck on Build 26040 or Build 23620, and another in which colors in the Performance section aren’t displaying correctly in dark mode.
(Get more info about Windows 11 Insider Preview Build 26241.)
Windows 11 Insider Preview Build 22635.3785Release date: June 14, 2024
Released to: Beta Channel
In this build, those in the Beta Channel who have turned the toggle on to receive the latest updates can right-click on apps pinned to the Start menu to see jump lists for apps that have them, such as PowerPoint. They can also more easily share content to an Android device from the Windows share window. Note that these and other new features are being gradually rolled out so are not yet available for everyone.
Those who have turned the toggle on to receive the latest updates also get a number of bug fixes, including for a bug in which clicking your profile icon on the Start menu and choosing Change account settings did not open account settings.
Everyone in the Beta Channel get a variety of bug fixes, including for a bug in which your system might have not been able to resume from hibernate after you turned on BitLocker.
There are seven known issues for everyone in the Beta Channel, including one in which Internet Information Services (IIS) and Windows Communication Foundation (WCF) may not work.
(Get more info about Windows 11 Insider Preview Build 22635.3785.)
Windows 11 Insider Preview Build 26120.961Release date: June 14, 2024
Released to: Dev Channel
In this build, those in the Dev Channel who have turned the toggle on to receive the latest updates get a small set of general improvements and fixes that improve the overall experience of running Windows.
(Get more info about Windows 11 Insider Preview Build 26120.961.)
Windows 11 Insider Preview Builds 22621.3807 and 22631.3807Release date: June 13, 2024
Released to: Release Preview Channel
In this update, Copilot will be pinned to the taskbar and will behave like an app so you can do things like resize, move, and snap the window. The build also lets you create 7-Zip and Tape Archive (TAR) files using the File Explorer context menu and adds support for Emoji 15.1. Note that those and other features are gradually rolling out and are not yet available for everyone. The Copilot features have not yet begun to roll out.
(Get more info about Windows 11 Insider Preview Builds 22621.3807 and 22631.3807.)
Windows 11 Insider Preview Build 26236Release date: June 12, 2024
Released to: Canary Channel
This build starts the rollout of the new account manager on Start menu. When you sign in with a Microsoft account, the new design gives you a quick glanceable view of your account benefits and makes it easy to manage account settings. In addition, it includes a small set of general updates and fixes that Microsoft says improves the overall experience of running Windows.
Several bugs have been fixed, including one that caused the preferred audio volume (under Settings > System > Sound > Volume Mixer) for Microsoft Edge to not persist across after restarting the app.
There are two known issues with this build, one in which some Windows Insiders in the Canary and Dev Channels are stuck on Build 26040 or Build 23620, and another in which colors in the Performance section aren’t displaying correctly in dark mode.
(Get more info about Windows 11 Insider Preview Build 26236.)
Windows 11 Insider Preview Build 22635.3720Release date: June 7, 2024
Released to: Beta Channel
In this build, those in the Beta Channel who have turned the toggle on to receive the latest updates can now use voice access to dictate text hands-free using Narrator. In addition, they get a new feature, auto restart for voice access in Windows 11, which automatically restarts voice access if it encounters any issues.
Those who have turned the toggle on to receive the latest updates get a number of bugs fixed, including one in which pressing Ctrl + F would sometimes not start a search in File Explorer.
There are seven known issues for everyone in the Beta Channel, including one in which Internet Information Services (IIS) and Windows Communication Foundation (WCF) may not work.
(Get more info about Windows 11 Insider Preview Build 22635.3720.)
Windows 11 Insider Preview Build 26120.770Release date: June 7, 2024
Released to: Dev Channel
In this build, those in the Dev Channel who have turned the toggle on to receive the latest updates get a small set of general improvements and fixes that improve the overall experience of running Windows. They also get an update of the Snipping Tool that introduces automatic save for screen recordings. Your recordings will automatically be saved to the Screen Recordings folder (inside your Videos folder). You can choose to turn this off in Snipping Tool settings.
(Get more info about Windows 11 Insider Preview Build 26120.770.)
Windows 11 Insider Preview Build 26231Release date: June 6, 2024
Released to: Canary Channel
In this build, Narrator users can now use voice access to dictate text hands-free. In addition, a new feature called auto restart for voice access in Windows 11 automatically restarts voice access if it encounters any issues so that individuals with limited mobility can get back to using voice access as quickly as possible.
The build also includes a variety of bug fixes and improvements, including several that increase Task Manager reliability.
There is one known issue with this build, in which some Windows Insiders in the Canary and Dev Channels are stuck on Build 26040 or Build 23620.
(Get more info about Windows 11 Insider Preview Build 26231.)
Windows 11 Insider Preview Build 26120.751Release date: May 31, 2024
Released to: Dev Channel
In this build, those in the Dev Channel who have turned the toggle on to receive the latest updates get the latest version of Copilot, which is pinned to the taskbar and runs like a traditional app, allowing you to resize, move, and snap the window. In addition, a new Linked devices page under Settings > Accounts allows you to manage PCs and Xbox consoles that you are signed into with your Microsoft account.
Everyone in the Dev Channel gets several bug fixes, including for a bug in which the Win + W keyboard shortcut did not work correctly to open the Widgets board, and another in which installation of Windows update failed to complete when you had to restart your device more than once.
(Get more info about Windows 11 Insider Preview Build 26120.751.)
Windows 11 Insider Preview Build 26227Release date: May 30, 2024
Released to: Canary Channel
In this build, Copilot for Windows runs as a traditional app pinned to the taskbar, allowing you to resize, move, and snap the window. The build also adds support for Emoji 15.1 and introduces a new Linked devices page under Settings > Accounts that allows you to manage PCs and Xbox consoles that you are signed in to with your Microsoft account.
Several bugs have been fixed, including one in which some apps didn’t run on startup even though they were enabled as startup apps in Settings, and another in which the Win + W keyboard shortcut did not work correctly and open the Widgets board.
There is one known issue with this build, in which some Windows Insiders in the Canary and Dev Channels are stuck on Build 26040 or Build 23620.
(Get more info about Windows 11 Insider Preview Build 26227.)
Windows 11 Insider Preview Build 22635.3646Release date: May 23, 2024
Released to: Beta Channel
In this build, those in the Beta Channel who have turned the toggle on to receive the latest updates get, in Microsoft’s words, “a small set of general improvements and fixes that improve the overall experience” of using Windows.
Everyone in the Beta Channel gets a number of bug fixes, including for a bug in which File Explorer stopped responding when you swiped from a screen edge after you turned off edge swiping, and another in which TWAIN drivers stopped responding when used in a virtual environment.
There are six known issues in this build, including one in which Internet Information Services (IIS) and Windows Communication Foundation (WCF) may not work.
(Get more info about Windows 11 Insider Preview Build 22635.3646.)
Windows 11, version 24H2 (Build 26100.712)Release date: May 22, 2024
Released to: Release Preview Channel
This build is a preview of the annual Windows 11 feature update to be released later this year. It includes a variety of new features, including HDR background support, energy saver, Sudo for Windows, Rust in the Windows kernel, support for Wi-Fi 7, and voice clarity, among others. In it, Copilot will also become a traditional app that can be pinned to the taskbar. Microsoft will be sharing details about all its features in the coming months.
Note that new AI features such as Recall announced by Microsoft earlier this week will not be available on your PC after installing this update, as they require a Copilot+ PC. For more information on those new AI features and Copilot+ PCs, see Microsoft’s blog post.
(Get more info about Windows 11, version 24H2.)
Windows 11 Insider Preview Build 26120.670Release date: May 17, 2024
Released to: Dev Channel
In this build, those in the Dev Channel who have turned the toggle on to receive the latest updates get a small set of unspecified “improvements and fixes that improve the overall Windows experience.”
Everyone in the Dev Channel gets several bug fixes including for a bug in which the Network Locations header was missing in the This PC section of File Explorer, and another in which NTLM authentication traffic might have increased in domain controllers (DC).
There is one known issue in this build, in which the Windows key + W keyboard shortcut may not work correctly to open the Widgets board.
(Get more info about Windows 11 Insider Preview Build 26120.670.)
Windows 11 Insider Preview Build 22635.3640Release date: May 17, 2024
Released to: Beta Channel
In this build, those in the Beta Channel who have turned the toggle on to receive the latest updates get support for Emoji 15.1, which introduces a small number of new emoji, and support for creating 7-zip and TAR archives in addition to ZIP via the context menu in File Explorer. The build also fixes several bugs for those who have the toggle turned on, including a few accessibility issues in File Explorer’s Common File Dialog.
Everyone in the Beta Channel gets several bug fixes, including for the underlying cause of the Start menu crashing on launch or the All apps list not displaying.
There are five known issues for everyone in the Beta Channel, including one in which Internet Information Services (IIS) and Windows Communication Foundation (WCF) may not work.
(Get more info about Windows 11 Insider Preview Build 22635.3640.)
Windows 11 Insider Builds 22621.3668 and 22631.3668Release date: May 17, 2024
Released to: Release Preview Channel
This build for Windows version 22H2 (Build 22621) and version 23H2 (Build 22631) adds several new features, including one that lets you directly share to specific Microsoft Teams channels and group chats in the Windows share window, if you sign in using a Microsoft Entra ID.
It also starts the rollout of the new account manager on the Start menu, which shows you your account benefits a glance and makes it easier to manage your account settings when you use a Microsoft account to sign in to Windows.
These features might not be available to all users yet, because they will roll out gradually.
The build also fixes a variety of bugs, including one in which File Explorer stopped responding when you swiped from a screen edge after turning off edge swiping.
(Get more info about Windows 11 Insider Builds 22621.3668 and 22631.3668.)
Windows 11 Insider Preview Build 26217Release date: May 15, 2024
Released to: Canary Channel
This build includes, in Microsoft’s words, “a small set of general improvements and fixes that improve the overall experience for Insiders.”
It also fixes two bugs, including one in which after using the Disable button for a camera under Settings > Bluetooth & Devices > Cameras, the Enable button wouldn’t work; and the other in which the text showing the color filters keyboard shortcut was missing from Settings > Accessibility > Color filters.
Microsoft is investigating reports that some Windows Insiders in the Canary and Dev Channels are stuck on Build 26040 or Build 23620. If that happened to you and you want to get the latest build in the Canary or Dev Channel, download the latest ISO, do a clean install, and opt your device back into flighting in the Canary or Dev Channels.
(Get more info about Windows 11 Insider Preview Build 26217.)
Windows 11 Insider Preview Build 22635.3575Release date: May 10, 2024
Released to: Beta Channel
In this build, those in the Beta Channel who have turned the toggle on to receive the latest updates can copy files from the Windows share window by clicking the new copy button. The build also fixes several bugs for those who have the toggle turned on, including one in which the address bar dropdown appeared unexpectedly on its own, because focus moved to the address bar.
There are five known issues for everyone in the Beta Channel, including one in which Internet Information Services (IIS) and Windows Communication Foundation (WCF) may not work.
(Get more info about Windows 11 Insider Preview Build 22635.3575)
Windows 11 Insider Preview Build 26120.470Release date: May 10, 2024
Released to: Dev Channel
In this build, those in the Dev Channel who have turned the toggle on to receive the latest updates get a new Game Pass recommendation card on the Settings homepage. The card will be shown to you if you actively play games on your PC.
Everyone in the Dev Channel gets a wide variety of bug fixes, including one in which IT admins can now use mobile device management (MDM) to turn off the prompt that appears when users sign in to an Entra-joined machine. To do this, they can turn on the “DisablePostLogonProvisioning” policy setting. After a user signs in, provisioning is off for Windows 10 and Windows 11 devices.
(Get more info about Windows 11 Insider Preview Build 26120.470.)
Windows 11 Insider Preview Build 26212Release date: May 8, 2024
Released to: Canary Channel
In this build, you can now generate QR codes for URLs and cloud file links through the Windows share window in order to share web pages across your devices. To do it in Microsoft Edge, click the share button in the Edge toolbar and choose “Windows share options.”
The build also fixes a variety of bugs, including one in which File Explorer sporadically crashed when using path suggestions in the address bar.
Microsoft is investigating reports that some Windows Insiders in the Canary and Dev Channels are stuck on Build 26040 or Build 23620. If that happened to you and you want to get the latest build in the Canary or Dev Channel, download the latest ISO, do a clean install, and opt your device back into flighting in the Canary or Dev Channels.
(Get more info about Windows 11 Insider Preview Build 26212.)
Windows 11 Insider Preview Build 22635.3570Release date: May 3, 2024
Released to: Beta Channel
In this build, those in the Beta Channel who have turned the toggle on to receive the latest updates can duplicate a tab by right-clicking on a tab in File Explorer and also receive a wide variety of bug fixes, including one in which the address bar dropdown might appear unexpectedly while using File Explorer.
The build fixes several bugs for everyone in the Beta Channel, including one in which Copilot auto-launched unexpectedly after PCs restarted.
There are five known issues for everyone in the Beta Channel, including one in which Internet Information Services (IIS) and Windows Communication Foundation (WCF) may not work.
(Get more info about Windows 11 Insider Preview Build 22635.3570)
Windows 11 Insider Preview Build 26120.461Release date: May 3, 2024
Released to: Dev Channel
In this build, those in the Dev Channel who have turned the toggle on to receive the latest updates get a small set of general improvements and fixes that improve the overall experience of Windows. Everyone in the Dev Channel gets a bug fixed in which one in which Copilot auto-launched unexpectedly after PCs restarted.
There is one known issue with this build: some Insiders experience an install error 0x8007371B when trying to install Build 26120.461
(Get more info about Windows 11 Insider Preview Build 26120.461.)
Windows 11 Insider Preview Build 22635.3566Release date: April 26, 2024
Released to: Beta Channel
In this build, those in the Beta Channel who have turned the toggle on to receive the latest updates can now drag-and-drop files with a mouse between breadcrumbs in the File Explorer Address Bar. For everyone in the Beta Channel, widgets are no longer pixelated or fuzzy. In addition, widgets on the lock screen are more reliable.
The build fixes an assortment of bugs for everyone in the Beta Channel, including a memory allocation issue in the Host Networking Service (HNS) that caused high memory consumption. The bug also affected service and pod deployment and scaling.
There are seven known issues in this build, including one in which Internet Information Services (IIS) and Windows Communication Foundation (WCF) may not work.
(Get more info about Windows 11 Insider Preview Build 22635.3566.)
Windows 11 Insider Preview Build 22635.3500Release date: April 19, 2024
Released to: Beta Channel
This build begins the rollout of a new account manager on the Start menu for those in the Beta Channel who have turned the toggle on to receive the latest updates. When you sign in with a Microsoft account, the new design gives you a quick glanceable view of your account benefits and makes it easier to manage account settings.
In the build, everyone in the Beta Channel gets new navigation bar on the left allowing one to switch between a dedicated widgets dashboard and other integrated dashboards like Discover.
There are several known issues in this build for everyone in the Beta Channel, including one in which Internet Information Services (IIS) and Windows Communication Foundation (WCF) may not work.
(Get more info about Windows 11 Insider Preview Build 22635.3500.)
Windows 11 Insider Preview Build 26200Release date: April 19, 2024
Released to: Canary Channel
In this build there are several improvements to the Widgets button on the taskbar so that the icons on the taskbar are clearer. There are also a larger set of animated icons.
Several bugs have been fixed, including one that caused RemoteApp windows to get cut off when using 200% scaling.
There are four known issues with this build, including one in which using Windows Ink to write in Copilot will not work with the updated Copilot in Windows feature that allows Copilot to act like a normal application window.
(Get more info about Windows 11 Insider Preview Build 26200.)
Windows 11 Insider Preview Build 22635.3495Release date: April 12, 2024
Released to: Beta Channel
In this build, those in the Beta Channel who have turned the toggle on to receive the latest updates will get recommendations for apps from the Microsoft Store under Recommended on the Start menu. This will appear only for Windows Insiders in the Beta Channel in the US and will not apply to commercial devices (devices managed by organizations). This can be turned off by going to Settings > Personalization > Start and turning off the toggle for “Show recommendations for tips, app promotions, and more.”
In the build, everyone in the Beta Channel can switch between two ways of using Copilot for Windows: The existing “docked” behavior that attaches Copilot to the side of your desktop, and a new mode where it acts like a normal application window that you can resize and move around your screen.
There are several known issues for everyone in the Beta Channel, including one in which Internet Information Services (IIS) and Windows Communication Foundation (WCF) may not work.
(Get more info about Windows 11 Insider Preview Build 22635.3495.)
Windows 11 Insider Preview Builds 22621.3520 and 22631.3520Release date: April 11, 2024
Released to: Release Preview Channel
This update adds a new mobile device management (MDM) policy called “AllowScreenRecorder” for the Snipping Tool. With it, IT admins can turn off screen recording in the app. The build also adds support for Arm64 .msi files using a Group Policy Object (GPO).
There are a wide variety of bug fixes in this build, including for a bug in which Settings stopped responding when you dismissed a flyout menu, and another in which the Windows Local Administrator Password Solution’s (LAPS) Post Authentication Actions (PAA) did not happen at the end of the grace period. Instead, they occurred at restart.
(Get more info about Windows 11 Insider Preview Builds 22621.3520 and 22631.3520.)
Windows 11 Insider Preview Build 22635.3430Release date: April 5, 2024
Released to: Beta Channel
In this build, those in the Beta Channel who have turned the toggle on to receive the latest updates get a Copilot feature in which when you copy text or image files, the Copilot icon will change appearance and animate to indicate that Copilot can help. When you hover your mouse over the Copilot icon, it will provide a menu of actions that you can take, such as creating a similar image or analyzing an image. If you select an action on the menu, it will launch the action with Copilot.
There are several known issues for everyone in the Beta Channel, including one in which Internet Information Services (IIS) and Windows Communication Foundation (WCF) may not work.
(Get more info about Windows 11 Insider Preview Build 22635.3430.)
Windows 11 Insider Preview Build 26100Release date: April 3, 2024
Released to: Canary and Dev Channels
This build fixes a variety of bugs, including one that prevented bringing focus to the “…” or refresh buttons within Copilot when using a keyboard (for example, by using tab to cycle through buttons).
There are four known issues with this build, including one in which Copilot in Windows does not always fill the width of the panel when docked and resized to a large width. Resizing Copilot to less than half of the width of your screen usually fixes this issue.
Note: The Canary and Dev Channels receiving the same builds is only temporary. During the period in which they are on the same builds, Insiders in the Canary Channel can switch to switch to the Dev Channel. Soon, the Canary Channel will jump to higher build numbers and the window will be closed for switching.
(Get more info about Windows 11 Insider Preview Build 26100.)

Deepak Jain, CEO of a Maryland-based IT services firm, has been indicted for fraud and making false statements after allegedly falsifying a Tier 4 data center certification to secure a $10.7 million contract with the US Securities and Exchange Commission (SEC).
The charges, filed by the US Department of Justice (DOJ) and made public on Wednesday, claim that Jain and his co-conspirators deceived the SEC by creating a fictitious certifier, “Uptime Council,” to falsely verify his firm’s data center as meeting the highest reliability standards.

Apple released a claustrophobic submarine movie for Apple Vision Pro earlier this month, and it gave me a sinking feeling.
The movie Submerged was neither augmented reality (AR) nor virtual reality (VR) nor 360-degree video. It was more like 180-degree video. According to reviews, the experience was as immersive as a submarine with a hole in it.
But wait a minute, you might say. I thought Apple Vision Pro was supposed to be mainly AR.
While the tech media and even the mainstream press point out that Apple Vision Pro sales aren’t anywhere near as high as Apple expected, a community of diehards still use the product heavily every day. The main rationale for these heavy users, the most practical and productive usage, is to expand the desktop of a MacBook Pro to gigantic proportions as AR displays floating in the air.
That general concept — using AR for desktop computing rather than video games, holographic hijinks, or teleportation meetings — is what Sightful’s Spacetop computing platform was all about.
The company’s Spacetop G1 was a one-of-a-kind augmented reality laptop that used AR glasses instead of a screen. The system displayed a virtual 100-in. display in front of the user anchored in space relative to the keyboard. The system ran on a proprietary Android-based operating system called SpaceOS; it functioned like a Chromebook, running apps from the cloud instead of desktop applications running from the device. I first told you about it in June.
I use the past tense here because, while the Spacetop G1 was scheduled to ship this month, it’s been killed off. The company emailed people who pre-ordered it and informed them their deposit would be refunded and the product would be canceled.
Instead, Sightful is now working on software that enables Windows PCs to project their displays onto Xreal’s AR display glasses, the same brand that shipped with the Spacetop.
Now, AR virtual desktops are a feature, not a productSightful has discovered that AR virtual desktop screens are a feature, not a product. Unfortunately, their offering will be limited and, essentially, unnecessary. While their integrated package was one-of-a-kind, their software will be joining a small but crowded market.
Xreal, for example, already supports both Windows and MacOS using its own Nebula software. (It’s unclear why users might want Sightful’s software instead of Xreal’s.) Viture One supports Windows and MacOS, enabling users to set up virtual displays in different configurations. TCL NXTWEAR S is compatible with Windows devices, allowing users to view their PC screen through the glasses. Lenovo ThinkReality A3 works with Windows machines to output virtual desktops with up to three virtual screens.And there are others.
Another interesting new product is the Visor, a lightweight spatial computing device vaguely similar to the Apple Vision Pro developed by Immersed, an Austin-based startup. It features two 4K OLED screens with a 100-degree field of view, 6DoF tracking, and hand and eye tracking capabilities. Weighing only 186g, it’s significantly lighter than competitors like the Meta Quest 3 and the Vision Pro.
And like the Vision Pro, Visor is VR, creating the illusion of AR via passthrough video.
Powered by the Qualcomm XR2+ Gen 2 chip, the Visor is designed primarily for productivity. It allows users to work with multiple virtual screens in both passthrough and fully virtual modes. That said, recent demos have shown issues with readability, heat management, and passthrough quality. The product gives users five HD screens on Windows, macOS, and Linux.
Starting at $1,050 for outright purchase, with a subscription model also available, the Immersed Visor is set to begin shipping limited “Founder’s Edition” units next month, with wider availability in April 2025. While promising, potential buyers should approach with caution, given the device’s ongoing development and the challenges observed in recent demonstrations.
The home run the industry hasn’t hit yetSome of the AR glasses mentioned above support hand gestures via sensors in the glasses, and most anchor the desktop screens fully in place.
Sightful’s Spacetop G1 had something going for it that none of these other solutions did: Integration with the laptop. The Spacetop G1’s keyboard base, which contained its own Qualcomm processor, served as a spatially tracked anchor for the AR glasses. This enabled the system to maintain a consistent positioning of the virtual displays relative to the physical keyboard.
The device had a depth camera mounted above the keyboard that tracked the user’s position relative to the keyboard and where they looked. This provided a significantly better AR experience when sitting in front of the keyboard.
The Spacetop G1 incorporated sensors that mapped the physical environment to ensure virtual elements were accurately anchored in the real world. And it used customized XREAL glasses, with cameras specifically designed to detect the Spacetop.
In summary, the system considered both the user’s position and the surrounding environment, and the glasses and the base unit worked together to improve screen anchoring and gesture control. Positioning sensors on a laptop and glasses is far better than on the glasses alone.
What we need from the industry is laptops with sensors built in and designed to work in concert with AR glasses for screen position, eye-tracking, and gesture control.
Apple doesn’t want to support cheaper, non-Apple solutions, so forget about Apple doing this. The Vision Pro experience is already amazing — though the price of admission is $3,500. (Apple is expected to ship lower-priced Vision Pro models next year at the earliest.)
The two best platforms for AR glasses supportThe two best platforms for dedicated hardware support for AR glasses are Windows and ChromeOS.
ChromeOS is especially interesting because that platform is often used by schools and others looking for very low-cost hardware. By optimizing AR glasses for virtual desktops, you not only get a very low-cost laptop, but also a very low-cost giant display. Or two. Or three.
Microsoft is uniquely positioned to offer Windows laptops with built-in AR glasses support using Microsoft-branded glasses. In fact, the entire Windows and Linux OEM market should be developing or partnering with companies that make AR glasses.
As a digital nomad who travels abroad while working and loves giant screens that are too big to carry, I’m super excited about virtual desktop screens. All we need now is to optimize the experience by laptop-glasses integration.
Sightful had the right idea, but it may have been the wrong company. It’s extremely difficult for a startup to enter the PC market with a usage model that has yet to be tried. That kind of leap can normally come only from an established giant with money to burn.
Speaking of which, somebody [cough!] Google! [cough!] should buy Sightful, its five or so patents, two founders, 60 employees, and vision for AR laptops, and convert their ideas into a mainstream OS, such as ChromeOS.
AR is definitely going to happen. The concept of using it to give tiny laptops gigantic virtual screens is also going to happen. We need the industry to optimize and mainstream this idea so that it doesn’t belong exclusively to a few hundred thousand Apple Vision Pro enthusiasts.
Laptops should just come with the built in sensors and OS support, with the glasses available separately as just another display option. A high-quality experience with virtual desktop screens in a laptop shouldn’t cost $7,000 (the combined price of a Macbook Pro plus Apple Vision Pro). It should cost $700 for a low-end Chromebook and $1,000 for a Surface laptop.
Virtual screens are far better for mobility, far better for the environment and far better for the wallet than giant physical displays. By improving the user experience (via laptop-embedded sensors and OS integration) and lowering the price, virtual screens could become serious mainstream options for how we all use our laptops.

Apple turned your iPhone into your wallet one decade ago. Ten years on, and the company continues to extend the digitization of personal payments, with small-scale loans, car rentals, and everything else that used to occupy space in your pocket.
In the face of regulatory pressure, the company recently agreed to open up some elements of its payment/wallet services. With that in mind, it is interesting to note some of the upcoming additions to the service that Jennifer Bailey, Apple’s vice president of Apple Pay and Apple Wallet, outlined in an extensive post to celebrate 10 years of Apple Pay.
In almost every case, those additions reflect wider support for third-party payments solutions, in particular those that provision similar deferred payment services to those briefly offered by Apple Pay Later.
What’s coming next from Apple’s wallet replacement schemesApple Pay has probably managed to become the world’s most widely used mobile payment service. Apple claims it has “hundreds of millions” of consumers in 78 markets, and notes that it is supported at checkout across tens of millions of websites, apps, and physical stores.
With that in mind, the new feature additions the company is promising for its service are likely to have some impact, particularly as over 11,000 banks also support use of Apple Pay. With that context, it may in future be seen as highly significant that by introducing support for in-app short term credit, Apple is kick-starting a business in casual loans.
Apple’s list of future additions includes:
Starting in iOS 18, Apple supports installment loans and payments. That means consumers can purchase items using short-term credit from Affirm and Klarna (US) and Monzo Flex and Klarna (UK) when they check out with Apple Pay online and in the app. Users in Canada will be able to use Klarna’s flexible payment options at checkout with Apple Pay online and in-app in the future. The company promises to introduce support to access installment payment options from eligible credit or debit cards when making online purchases with Apple Pay in the US with Citi, Synchrony, and across eligible, participating Apple Pay issuers with Fiserv; in Australia with ANZ; in Singapore with DBS; in Spain with CaixaBank; and in the UK with HSBC, NewDay, and Zilch, with more issuers to follow. US Apple Pay users can redeem rewards with eligible Discover credit cards when they check out with Apple Pay. Support for other issuers will follow. In some markets, Apple Pay is now also available when using third-party browsers so long as they offer support for WebSockets. Adding cards has been improved with Tap to Provision, which lets users add a credit or debit card to Apple Wallet by tapping an eligible card to the back of their iPhone. Next year, customers in the US will also be able to see their PayPal balance when using their PayPal debit card in Apple Wallet. In a rare interview to mark the anniversary, Bailey also hinted at other future services, including an extension to the company’s digital car key service for car rental firms. “Being able to book a car rental, confirm your authentication and identity … you can imagine that a car rental company is going to issue you a digital key, and that key could be used to unlock and use a car,” she said. The security thingThat Apple is being forced to open up aspects of its business may pose challenges along the way, principally around security and privacy when using these systems.
“We’re always looking for new ways to make using Apple Wallet convenient while delivering unparalleled security and peace of mind,” the Apple Pay chief said.
“We know how important it is for customers to feel secure and trust that their financial transactions are private when making a payment. That’s why we’re always working to safeguard consumers, while also enabling banks to have industry-low levels of fraud for Apple Pay transactions. And it’s also why Apple Pay was designed to protect users’ highly sensitive personal and financial information, like their card number, which is never shared with merchants. Our customers trust that when they use Apple Pay anywhere, they can have the peace of mind that their payments are protected.”
The company’s ability to provide a point of trust is a significant asset to any digital payments business, and the path toward that kind of card-free future is already peppered with illustrations of what’s at stake when even credible companies see security undermined. In London, UK, for example, public transport operator Transport for London (TfL) recently suffered an attack in which customer data, including payment and password details, may have been exfiltrated. That incident took elements of TfL’s operations offline for weeks.
The evolution of the digital walletConsumer confidence, high usage, and market-proven security mean Apple continues to extend the reach of the service, which opened up its last new market in September when iPhone users in Oman became able to switch on the service. Digital payments in that nation have been accelerating thanks to a push to them from the Central Bank of Oman.
Meanwhile, Apple also continues to convert holdouts such as Home Depot and H-E-B, both of which finally introduced support for Apple Pay in the US over the last few weeks.
The move to digital everything has accelerated even as Apple Pay has progressed. Just a decade ago, US consumers were quite resistant to mobile payments, though engagement was far higher across the water in Europe.
However, Apple Pay’s release coincided with a major investment in mobile bandwidth across North America, and as that infrastructure rolled out, consumers began to vote with their fingers and use digital payments more.
But it’s not just payments. Recent data from PYMNTS Intelligence found that US consumers now engage in an average of 14 different digital payment-related activities every month, from bill payments to telehealth to ordering groceries or entertainment services.
Of course, this engagement with digital payments for things we already do also sets the foundations for the emergence of additional digital-only services.
With that in mind, any business leader should consider the extent to which habituation with digital process creates wider opportunity for digitization across product and services development and how your business works internally. “Networks will become the catalyst for growth, profits and scale because they have the power to connect stakeholders and simplify and monetize value exchange,” wrote PYMNTS contributor and Market Platform Dynamics CEO Karen Webster.
What next?If you think about it, the move to digital payments, and the repercussions of doing it, make even more sense retrospectively. After all, when Apple set out to replace your wallet all those years ago, that replacement also meant the company’s products and services digitized the most personal parts of most people’s existence: identity, keys, payments, mass transit — even riding a bike.
Today, with so much that can be defined as personal having become digitized, it is more vital than ever that Apple succeeds in its mission to protect user privacy and security while also offering the personal convenience of the digital wallet. At the same time, this also means that at a very core level, digital identity has been unleashed and fresh opportunity knocks, even as mobile banking remains a top three digital activity across most nations.
Next step? B2B payments, probably, given that banking regulation, antiquated internal ordering systems, and lack of service provision mean that in some markets just 30% of enterprise payments made are digital, even while 70% of transactions take place online. In other words, now that wallets are digital, there’s still plenty of room to innovate and grow.
Please follow me on LinkedIn, Mastodon, or join me in the AppleHolic’s bar & grill group on MeWe.

No Android 15? No problem. You can still enjoy some of the fancy new features from Google’s latest Android version — no matter who made your current device or how old it might be.
Android 15 officially landed in the world with a bit of a thud in early September, when Google released the software’s source code, but the first real rollout only just got going this week — with current Pixel devices, as usual, being at the front of the pack.
How long it’ll take other Android device-makers to follow suit is, as always, an open question. (Seriously — have you seen my breakdowns over time?!) But while we can’t force those companies to make timely software support more of a priority, we can get out ahead of ’em and get creative to bring some Android-15-inspired splendor your way.
Here, specifically, are seven Android 15 features you can add onto any Android phone today — along with two bonus features that were under development but didn’t quite make the cut into this latest Android update.
Get ready for a massive upgrade to your Android experience — no official rollouts needed.
[Psst: Want even more advanced Android knowledge? Check out my free Android Shortcut Supercourse to learn tons of time-saving tricks for any phone you’re using.]
Android 15 feature #1: Private SpaceUp first is the highest profile new Android 15 feature — and, in many ways, the easiest one to emulate on devices that aren’t yet running Android 15.
It’s called Private Space, and it’s essentially a way to add an extra layer of security onto sensitive apps or apps with especially important info. You can require authentication to open such apps and even hide ’em completely out of sight in a special locked-down area of your app drawer, if you really want to keep ’em tucked away.
JR Raphael, IDG
📲 To bring the feature onto a non-Android-15 device: First, if you’re using a phone made by Samsung or OnePlus, it’s likely you already have a similar sort of feature on your device and just waiting to be found! Try searching your system settings for either secure folder or app lock to see if it’s there.
Otherwise, a third-party app called Applock Pro can bring something similar onto any Android gadget. It isn’t quite as secure as an operating-system-integrated option, since someone could technically uninstall it. But it’s the next-best thing, and it has some mechanisms for masking itself to minimize the odds of anyone even noticing its presence.
Android 15 feature #2: App pairsOne of the most useful Android 15 features is the ability to create preset pairs of apps that then open together in a ready-to-roll split screen with just a single tap on your home screen.
srcset=”https://b2b-contenthub.com/wp-content/uploads/2024/10/google-pixel-android-15-app-pairs.webp?quality=50&strip=all 750w, https://b2b-contenthub.com/wp-content/uploads/2024/10/google-pixel-android-15-app-pairs.webp?resize=300%2C290&quality=50&strip=all 300w, https://b2b-contenthub.com/wp-content/uploads/2024/10/google-pixel-android-15-app-pairs.webp?resize=721%2C697&quality=50&strip=all 721w, https://b2b-contenthub.com/wp-content/uploads/2024/10/google-pixel-android-15-app-pairs.webp?resize=174%2C168&quality=50&strip=all 174w, https://b2b-contenthub.com/wp-content/uploads/2024/10/google-pixel-android-15-app-pairs.webp?resize=87%2C84&quality=50&strip=all 87w, https://b2b-contenthub.com/wp-content/uploads/2024/10/google-pixel-android-15-app-pairs.webp?resize=497%2C480&quality=50&strip=all 497w, https://b2b-contenthub.com/wp-content/uploads/2024/10/google-pixel-android-15-app-pairs.webp?resize=372%2C360&quality=50&strip=all 372w, https://b2b-contenthub.com/wp-content/uploads/2024/10/google-pixel-android-15-app-pairs.webp?resize=259%2C250&quality=50&strip=all 259w” width=”750″ height=”725″ sizes=”(max-width: 750px) 100vw, 750px”>One tap to two apps, with Android 15’s new app pairs possibility.JR Raphael, IDG
📲 To bring the feature onto a non-Android-15 device: A thoughtful and delightfully simple little tool called Be Nice can bring this same exact power onto any Android device. Check out my complete guide to getting it going in a mere 20 seconds.
Android 15 feature #3: An idle-time control panelYour idly charging Android device is more useful than ever with Google’s new Android 15 Home Controls screen saver. And while the name may sound about as non-work-related as possible, don’t be fooled: You can fill that panel up with any combination of connected-device controls you want, ranging from thermostats to lights and all sorts of other workday-aiding points of easy access (especially if you’ve got a home office).
JR Raphael, IDG
📲 To bring the feature onto a non-Android-15 device: The aptly named Widget Screensaver app is the key to bringing this very same intelligence onto whatever device you’re using. Just set it up, following my guide, and be sure to select the Google Home “Favorites” widget during the configuration.
Android 15 feature #4: Theft protectionGoogle’s touting a trio of new theft protection features as part of its Android 15 rollout, but in actuality, you don’t need Android 15 to get any of those elements in your life.
📲 To bring the feature onto a non-Android-15 device: Read this guide to activating Google’s latest Android security enhancements, and you’ll be up and running with the official additions in a matter of minutes.
Android 15 feature #5: A fresh volume panelAndroid 15 adds a spruced-up volume panel into the operating system — with larger, more easily adjusted sliders for specific sorts of media volumes as well as a more prominent button to shift your phone’s audio output from the phone itself to any connected devices.
JR Raphael, IDG
📲 To bring the feature onto a non-Android-15 device: The secret here is a saucy little app called Precise Volume 2.0. It replaces your standard system volume panel with a completely customizable alternative — and, as I outline in this easy-to-follow guide, one of its options is emulating the Android 15 volume interface.
Android 15 feature #6: Expanded app namesA small but welcome feature in Android 15 is a new toggle within Google’s Pixel Launcher settings that lets you stop the system from cutting off the names of longer apps in your app drawer.
It’s a subtle touch, for sure — but man, is it a nice one.
📲 To bring the feature onto a non-Android-15 device: Most custom Android launchers offer similar sorts of controls. I’d look at the time-tested Nova Launcher, if you’re aiming to create something close to a standard setup but with lots more flexibility.
Android 15 feature #7: App archivingWhen you’ve got an app you aren’t actively using but don’t want to uninstall entirely, Android 15 can archive it for you — meaning the software compresses it, in a sense, and keeps the core files present while removing lots of space-taking and permission-requiring elements.
Then, if you ever want to use the app again, you can simply restore it and pick right back up where you left off.
📲 To bring the feature onto a non-Android-15 device: This one’s easy — ’cause in a rarely realized twist, the same sort of system actually launched as a feature of the Android Play Store last year! Just open up the Play Store on your device, tap your profile picture in the upper-right corner, and select “Settings.” Then, tap the “General” section and look for the “Automatically archive apps” toggle to fire up the system and get it going.
Android 15 bonus feature #1: Notification cooldownOne of the most intriguing under-development Android features is something that didn’t ultimately make the cut for Android 15 but may show up in a future quarterly update or perhaps even another Android version down the line — and that’s something Google’s calling notification cooldown.
It’s an option to “gradually lower the notification volume when you get many successive notifications from the same app” — either in general or specific only to notifications that are considered “conversations.” That way, when someone messages you in a rapid-fire style, you can avoid getting annoying alert after annoying alert at a rate of one ding per every seven seconds.
📲 To bring the feature onto a non-Android-15 device: As long-time Android Intelligence readers know, you can grant yourself that very same sanity-saving superpower with even more versatility on any device right now — if you know where to look.
Android 15 bonus feature #2: Lock screen widgetsAndroid 15 had been rumored for a while to reintroduce the concept of lock screen widgets — more than a decade after the feature was first launched and then promptly killed for no apparent reason.
While that hasn’t yet happened and seems to be something being saved for a future release, you can give yourself that same efficiency-enhancing ability this second on any Android device — with far more flexibility and compatibility than Google’s own native system is even likely to provide.
📲 To bring the feature onto a non-Android-15 device: Follow the steps in this Android lock screen widgets guide, and get ready to enjoy levels of advanced awesomeness few mere mortals ever encounter.
And there ya have it — seven Android 15 features and two extra features not even present in Android 15 that are at your fingertips today. You may be waiting a while longer yet for Android 15 itself to reach you, but with these readily available upgrades, you won’t be missing out on too much in the meantime.
Get even more advanced experience-enhancing knowledge with my free Android Shortcut Supercourse. You’ll learn tons of time-saving tricks!

The Cybersecurity Association of China (CSAC) has urged a security review of Intel products sold in the country, claiming the US semiconductor firm poses ongoing threats to China’s national security and interests.
In a statement posted on its WeChat account, CSAC said that Intel’s major product quality and security management flaws indicate its extremely irresponsible attitude toward customers.
CSAC is an industry body, but its allegations raise concerns >about a potential security review and subsequent action by the country’s cyberspace regulator, the Cyberspace Administration of China (CAC). Last year, CAC banned products from Micron, citing national security risk.
Significantly, this year Intel has secured orders for its Xeon processors from several Chinese state-affiliated agencies for AI applications, according to Reuters.
This action marks the latest chapter in the ongoing trade conflict, which has seen US administrations ban Chinese-made hardware from domestic networks and impose export controls to limit China’s access to advanced computing technologies.
Impact on Intel and the industryA ban could deal a significant blow to Intel, already struggling with financial challenges, a shrinking market share, and layoffs. It could also affect Chinese companies that are already contending with US export restrictions.
“If the CAC decides to take more drastic action than it did with Micron, Intel could face significant challenges with its sales and market share in China,” said Thomas George, president of Cybermedia Research. “This situation also poses a risk for the numerous companies in China that rely on Intel chips for high-performance computing (HPC), which is essential for scientific research, financial services, and even national security.”
A potential review and subsequent action from the CAC could substantially impact Intel’s strategies and market position, while also reshaping the strategic considerations of other key players in the semiconductor industry, George noted.
Other analysts also highlight that the broader impact would likely extend beyond Intel, affecting the industry as a whole.
“The sanctions will definitely have repercussions and a short-term impact on Intel,” said Pareekh Jain, CEO of Pareekh Consulting. “But although rivals like AMD might see some initial benefit, eventually they will likely be targeted as well. The medium-term goal seems to be to bolster China’s domestic chip industry.”
Speculations on Chinese companiesChina has been pushing for self-sufficiency in the semiconductor sector, recently urging domestic car manufacturers such as SAIC Motor, BYD, Dongfeng Motor, GAC Motor, and FAW Group to boost their sourcing of automotive-related chips from local suppliers.
“Chinese firms like Huawei and Alibaba are accelerating their investments in semiconductor technologies,” George said. “Despite these ambitions, the readiness and capability of domestic alternatives to match Intel’s offerings remain uncertain.”
One potential way for US companies to overcome this challenge would be to invest more in China, Jain suggested, citing Tesla as an example.
“This strategy would demonstrate a commitment to the Chinese market and may provide some protection from retaliatory actions,” Jain added. “Essentially, US companies can position themselves as commercial entities with interests in China, separate from US government actions.”

Corporate law is nothing like you see on television. To prepare for a case, 150 attorneys might be tasked to travel to remote warehouses to comb through tens of millions of documents gathering dust or track down amorphous electronic communications. It’s a process known as discovery.
For more than a decade, law firms have been using machine learning and artificial intelligence tools to help them hunt down paper trails and digital documents. But it wasn’t until the arrival two years ago of OpenAI’s generative AI (genAI) conversational chatbot, ChatGPT, that the technology became easy enough to use that even first-year associates straight out of law school could rely on it for electronic discovery (eDiscovery).
Today, you’d be hard pressed to find a law firm that hasn’t deployed genAI, or isn’t at the very least kicking the tires on its ability to speed discovery and reduce workloads.
For all intents and purposes, no one practicing law today studied AI in school, which means it falls to firms to integrate the fast-evolving tech into their workplaces and to train young lawyers on matching AI capabilities to client needs while remaining accountable for its output. This is the essence of turning AI into a copilot for all manner of chores, from wading through data to analyzing documents to improving billing.
In that vein, longtime IT workers are no longer just on call for computer glitches and AV setups; they have moved to the forefront of running a law firm, handling AI’s role in winning cases, retaining clients, growing revenue and, inevitably, helping attract the best and brightest new talent. Multinational law firm Cleary Gottlieb is a prime example of that.
Cleary has been able to dramatically cull the number of attorneys used for pre-trial discovery and has even launched a technology unit and genAI legal service: ClearyX. (ClearyX is essentially an arbitrage play — an alternative legal service provider [ALSP] for offshoring eDiscovery and automating electronic workflows.)
While Cleary readily admits that genAI isn’t perfect in retrieving 100% of the documents related to a case or always creating an accurate synopsis of them, neither are humans. At this point in the technology’s development, it’s good enough most of the time to reduce workloads and costs.
Still, cases do pop up that can be more expensive when customizing a large language model to suit specific needs than deploying those dozens of eager attorneys seeking to prove themselves.
Computerworld spoke with Christian “CJ” Mahoney, counsel and global head of Cleary’s e-Discovery and Litigation Technology group, and Carla Swansburg, CEO of ClearyX, about how the firm uses genAI tools. The following are excerpts from that interview:
Why is AI being adopted in the legal profession? Mahoney: “Because the legal profession is seeing an explosion of information and data created by their clients, and it’s become increasingly challenging to digest that information strictly through a team of attorneys looking through documents. That explosion probably started two decades ago. It’s been growing more and more challenging.
“I just had a case where we were measuring the amount of data we looking at, and for one case, we had 15 terabytes we had to analyze. It was over 50 million documents, and we had to do it in matter of weeks to find out what had to provide to the opposing party.
“Secondly, we wanted to find out what’s interesting in documents and what supported our advocacy. Traditional ways for looking through that type of information and getting a grasp of the case is really not feasible anymore. You need to incorporate AI into the process for analysis now.”
Swansburg: “One of the big shifts with OpenAI and genAI, in particular, is for the first time there’s ubiquity. Everyone’s hearing about it. Secondly, sophisticated clients are starting to approach it — even the formerly untouched Wall Street firms and other large firms with an eye on cost sensitivity.
“Fast forward to now. There’s a bit of an expectation that with the advent of genAI, things should be quicker and cheaper. Second of all, [there’s] the accessibility of AI through natural language processing. The third thing is the explosion of purpose-designed tools for the legal profession, and that does go back about a decade when you had diligence tools and tools for contract automation.”

Christian “CJ” Mahoney, counsel and global head of Cleary’s e-Discovery and Litigation Technology group, and Carla Swansburg, CEO ClearyX
Cleary Gottlieb
How have the expectations of clients changed regarding the use of genAI? Swansburg: “A year-and-a-half ago, we were getting messaging from clients saying, ‘You’d better not be using AI because it seems really risky.’ Now, we’re getting requests from clients asking, ‘How are you using AI to benefit me and how are you using it to make your practices more efficient for me?’
“There’s a lot of changing dynamics. Legal firms that were historically reluctant to embrace this technology are asking for it — ‘When can I get some of this generative AI to use in my practice?’”
How has the job of an attorney changed with genAI? Swansburg: “Nobody went to law school to do this. I used to go through banker’s boxes with sticky notes as a litigator. Nobody wants to do that. Nobody wants to read 100 leases to highlight an assignment clause for you. The good thing is [genAI is] moving up the value chain, but it’s starting with things that people really don’t want to be doing anyways.”
Is genAI replacing certain job titles, filling job roles? Mahoney: “I’d say we’re not to the place where it’s replacing entire categories of jobs. It’s certainly making us more efficient such that if I would have needed a team of 60 attorneys on work I’m doing, I may need a team of about 45 now. That’s the type of efficiency we’re talking about.
“I had over 60 [attorneys] just this weekend working on just one case. It’s the big data explosion of evidence there is to comb through.
“We’re using more complex workflows using AI. I said I saw a 60-person to 45-person reduction. But, on this kind of case, I would have had probably 150 attorneys doing this 15 years ago. Back then, it would just be like ‘OK guys, here’s a mountain of evidence — go through it.’
“Now, we are using several AI strategies to help classify documents for what we need to turn over to help narrow the amount of content we have to look over. It’s helping us to summarize before we even look at the documents, so that we have a summary going in to help us digest the information faster.”
Swansburg: “In my world, it’s not really replacing jobs yet, but it’s changing how you do jobs. So, it’s allowing people to move up the value chain a little bit. It’s taking away rote and repetitive work.
“Our experience has been — and we’ve kicked tires on a lot of language models and purpose-designed tools — [genAI tools] are not good enough to replace people for a lot of the work we do. For something like due diligence…, you often must be right. You need to know whether you can get consent to transfer something. In other use cases, such as summarization and initial drafting, that sort of thing is a little more accessible.”
What does that big data you’re discovering look like? Is it mostly unstructured? Mahoney: “Most of my data sets are unstructured. We’re talking about email and messages on someone’s laptop or a portion of a document repository on a file server. These days, we’re talking about chats on platforms like Teams or mobile devices. Often, we’ll target those collections through good attorney investigations, but a lot of times we have unstructured data sources like mailboxes to comb through. What we’re doing there is use a large language model algorithm.
“We are reviewing some samples, some of them random and some of them with training approaches we developed to target documents we think will help the model understand what we’re trying to teach it quicker. We’re reviewing a few thousand documents to train the model to predict if a document is responsive to the other [opposing] side’s document requests. We’re then running that model over millions of documents. We find throughout iterative model training improvement processes, we are approaching and sometimes surpassing the type of performance we’d expect by that team of 150 attorneys looking at all these documents.
“So, we use that as our starting point and sometimes our only process for identifying what we need to deliver to the other side. But once we have that set, we are using similar processes to identify things like attorney-client privilege in the document. And again, to identify which of these documents are interesting and useful for our advocacy.
“Now we’re also coupling that with generative AI workflows where, in addition to this training strategy, we’ve identified small samples of the [document] universe; we’re also seeing prompt-based genAI queries on portions of the data set to find documents that support our advocacy.”
Have you found other uses for AI that you didn’t initially expect? Mahoney: “We’re using genAI to look at files that we could have never used old school keyword searches on because they don’t have any text in them. They could be images or movies. We created a genAI process using some of the really new algorithms out there to analyze things like images and video files for finding more interesting information.
“We’ve also created genAI workflows when we claim attorney-client privilege; we have to create a whole attorney-client privilege log. We’ve created genAI workflows to help us draft the privilege log. It’s the same concept as using genAI to summarize a document. We’re using it to summarize the privileged portion of a document, but summarize it in a way that we’re meeting our privilege log obligation without revealing what the privilege advice is.
“Then a lot of our human-in-the-loop practices are taking a look of those AI results and doing validation, making some improvements here and there, rather than relying entirely on the AI. The level of that validation depends on what the task is.”
AI has the tendency to go off the rails with errors and hallucinations. How do you address that? Swansburg: “In CJ’s world, they work off of percentages — like 80% accurate. For us, largely we need to be 100% accurate. A lot of what we do, whether it’s contract analysis and management or transactional diligence, we have a context set of materials. So, the potential for hallucinations is more limited. Having said that, some of the tools in market will still hallucinate. So, you’ll say, ‘Find me the address of the leased property’ and it’ll totally make something up.
“One of the key things we do, and some of the development work we’re doing, is to say, ‘Show me in the document where that reference is.’ So, there’s a quick and easy way to validate information. You’ve got a reference; you tell me what it says. You’re extracting a piece of it, so we have a really fast way to validate.
“For us, it’s always a discrete set of context documents. So, we can first of all solve through prompting and tailoring it to which set of documents they want us to use, but second of all always confirming there’s always a way to ensure the provenance of the information.
“Some of the work we’re doing is we’ve developed a way to prompt a model to tell us when the termination data of an NDA is? If a person’s reading it, they can usually tell. But NDAs have an effective date and then they have a term that can be written in any number of ways: two years, three years, and then there are often continuing obligations.
“So if you just said, ‘When does this NDA terminate?’ a lot of AI models will get it wrong. But if you generate a way to say, ‘Find me the effective date, find me a clause, find me the period of time or continuing obligations,’ it’s typically 100% accurate. It’s a combination of focused context documents, proper prompt engineering and a validation process.”
Are you using retrieval augmented generation (RAG) to fine-tune these models, and how effective has it been at that task? Mahoney: “We are using RAG to put guardrails on how the large language model responds and what it’s looking at in its response. I think at times that’s certainly a helpful tool to use on top of the LLM.
“I’d also say even though we are more aggressively using LLMs and genAI in the discovery space, the process Carla described looks exactly the same. The difference would be our tolerance for errors, as part of that validation process.
“That’s comparing it to what human results would look like. What we find historically on various tasks in electronic discovery over several decades — humans usually get things right about 75% of the time. So, when we’re looking at LLMs and genAI, we want to be careful it’s working well, but we also want to be careful that we’re not holding it to too high a standard.
“If you’re writing a brief, 75% accuracy would be horrible and unacceptable. But when you’re looking through two million documents, that might be perfectly acceptable. That’s how the process looks a little different, even though the structure of the process looks the same in terms of steps.”
Small language models as opposed to large proprietary models from Amazon, Meta, and OpenAI are growing in popularity because you can create a model for every application need. What kinds of AI models do you use? Mahoney: “We’ve actually been using open large language models for five years now. We started with what was the largest language model at the time, but it’s probably closer to a small language model now. We use a version of BERT a lot when we’re doing supervised learning.
“We are very LLM agnostic, in that we’re able to look at the different tasks and see which one is right for a particular task. For image analysis, or the multimedia analysis, we’re using the latest and greatest, such as the ChatGPT Omni. It’s unique in having capabilities for drafting [client-privilege] log lines. Depending on the data, we’re shifting between GPT-4 or GPT-3.5 Turbo.
“We’re actually looking at where we’re getting reasonable performance and comparing that to things like costs.”
Is price an issue you consider when adopting a model? Mahoney: “Different LLMs have very different price points. For some of our data sets, the way GPT 3.5 Turbo is performing log lines is actually quite good. So, we wouldn’t want to spend the extra money on GPT-4 there.
“On the small language model front, I’d say we’re doing tuning rather than a separate small language model for each application…. We’re taking an existing model — but where we have an industry that might look very different than what that model was built on — [and] we’re doing some fine tuning on top of that to introduce the model to a dataset before it starts making predictions on it.”
So, essentially, some LLMs are better at some tasks than others? Mahoney: “Some language models are better at certain tasks in summarizing or pinpointing whatever it is. Ideally you have a workflow with six steps and you’re using a different LLM at different steps. You never know who’s going to emerge tomorrow and being better at X or Y.
“We’ve been using OpenAI [LLMs] before it was publicly launched. And we’ve been testing Meta and Claude and using the ones that we think make the most sense for a particular task.”
Data scientists and analysts, prompt engineers — what roles do you have or have you added to address your LLM needs? Swansburg: “For the work CJ does, and the work we do, the larger the data set, the more the need for data scientists. So, he does work with data scientists on his side.
“On my side, in terms of prompt engineers, we have good software developers that can do that for you. We have people who are pure developers, and we have people who sit in the middle that we call ‘legal technologists.’ Those are the translators who take client and lawyer requirements and feed those back and do the customization to the platforms we build.
“We don’t have any data scientists yet, because we use discrete data sets. So it’s more about being able to engineer the prompts — and the team we have now has been able to do that on the developer side. As we grow, and right now we’re recruiting another half-dozen developers, we will get more nuanced and look for people with prompt engineering experience and building APIs with LLMs and other tools.
“So, it’s constantly changing.”
Are you’re mostly using proprietary rather than open-source models? Mahoney: “Right now, we’re just using proprietary models and plugging them in and testing them — OpenAI being the more common example. We’re building things through prompts like contract determination dates to extract that data we need and building bundles of questions that will be generated based on the automatic determination of what the system in ingesting. All of that is being tested now.
“Some of them are really expensive. Something like ChatGPT is very accessible. Even the enterprise models can do the trick, and they’re accessible and affordable. “
If legal departments and law firms were already using AI and ML, why is ClearyX needed? Swansburg: “We’re trying to build a model that’s a lot less expensive than contract management software…and to have much higher quality than a lot of providers and provide a service.
“A lot of companies don’t have people to own and operate these programs. So, they have shelfware. They buy a contract lifecycle management tool, and it take three years to get their return on investment; then people don’t use it because it’s not custom designed. So, we’re trying to build custom solutions for clients that work the way they work, and that are affordable.
“We’re not venture capital owned. We’re owned by the partnership, so we’re able to build things in the right way. We’re not just serving clients of the Cleary law firm; we also have a mandate to get outside clients.
“We started thinking we weren’t going to be a development shop. We were going to use existing solutions and weave them together using APIs, but a couple things happened. The tools on the market weren’t doing what we wanted them to do. We weren’t able to customize them in the nuanced way that made clients actually delighted to use them.
“The other is the ubiquity of AI, and the ability to customize them is way easier than it was three years ago. So, over the last eight months or so, we’ve been able to pivot to something that allows us to customize it more easily and collaborate with clients to figure out how they want it to work.”

Apple just gave smaller enterprises a chance to compete on a more equal basis with larger concerns with three nice improvements to Apple Business Connect: Business Caller ID, brand identity in Mail, and custom business logos for use with Tap to Pay.
Together, the three tools mean that smaller businesses — now including enterprises that do not work from a set location — can deliver a more professional-seeming degree of service. For example, a small plumbing company can show its logo and contact details when making a call to a customer’s iPhone, or attach its brand identity to emails and messages received by clients so they can more easily identify genuine communications.
The solution also makes life much harder for phone scammers, as it adds another barrier to prevent them pretending to be bona fide enterprises.
What is Apple Business Connect?Apple Business Connect appeared in 2023, supplementing then existing integrations with Apple Maps that let brick-and-mortar businesses make themselves visible. The service then let business owners claim, edit, and manage location place cards and customize what business information appears in Maps (or in services that use data drawn from Maps, including Siri). Spaces called Showcases let business owners display images, offer online ordering, and provide other information to help draw attention to their business.
Apple’s system also offers an Insights page that provides historical information about how, and how many times, customers have already found you. This provides you with aggregated insights into what customers sought as they found you, a heat map to show you approximately where your customers are based, and the number of views your existing listing (if one exists at all) already generates via Apple’s system.
What are the new features in Apple Business Connect?The new features build on those tools and widen the service so that it can also be used to promote businesses that lack a physical location. Any verified business can now create a consistent brand and location presence, using the following tools:
Branded Mail: Businesses can display their brand name and logo in emails to customers, so they become more visible in Mail. Business users can sign up today, and the service will go live with the release of iOS 18.2. Tap to Pay: The brand name and logo can also be made visible when accepting payments through Tap to Pay on iPhone, so customers know they’re making a payment to a trusted and verified business. Business Caller ID: This feature means that when a business calls a customer’s iPhone, the business name, logo, and department will appear on the inbound call screen. This should help customers know which calls to respond to and help blunt the ongoing wave of annoying spam calls. This feature won’t be available until next year. What are the benefits of Apple Business Connect?The beauty of the service is that it is made available online and via Maps and supporting applications to over a billion people using iPads, iPhones, and Macs. Once a customer or potential customer gets to your business listing, they will find the information there easy to use and access, while your control of that listing lets you work to communicate the benefits of your business to that potential customer.
The added advantage of the Showcase section is that this can be tweaked to provide special offers, including one-time and time-limited offers, to help you win new customers once they reach your card. You can also monitor and optimize the performance of your listing and draw some SEO benefits from the existence of the information in the Apple ecosystem.
“We’re excited to offer all businesses — including those without a physical location — the ability to create a brand that appears across the Apple apps that over a billion people use every day,” David Dorn, Apple’s senior director of Internet Software and Services Product, said in a statement. “We designed Business Connect to empower businesses to present the best, most accurate information to Apple users. With today’s updates, we’re helping even more businesses reach customers, build trust, and grow.”
While an Apple Business Connect listing won’t necessarily transform your enterprise, it is free, simple, and far more likely to generate new business than the lack of any listing at all. In the future, these listings may become the basis of some kind of ad placement service within Maps.
How does my business join Apple Business Connect?Access to the service has been widened to include owners of virtual, online, and service businesses, as well as the brick-and-mortar businesses it already supported.
Business owners can sign their operation up to Apple’s service using their existing Apple Account (as Apple ID is now called). They can also create a new Apple Account for their business to use when signing up for the service.
Signing up is a straightforward process:
Visit the Apple Business Connect website from any smartphone, desktop, or laptop. Register using the relevant Apple ID. Apple will verify the business. Once verified, the business owner can claim any physical locations and begin updating and personalizing their place card. Businesses can also manage their location presence at scale through listing management agencies like DAC Group, Rio SEO, SOCi, Uberall, and Yext. The information is then made available via Maps, and through Apple and third-party apps that make use of data held in Maps.Apple has provided extensive guidance to help you make use of Apple Business Connect.
Please follow me on LinkedIn, Mastodon, or join me in the AppleHolic’s bar & grill group on MeWe.






























